Microsoft released security updates for 79 vulnerabilities in its September 2024 Patch Tuesday release. These vulnerabilities include four actively exploited vulnerabilities (CVE-2024-38014, CVE-2024-38217, CVE-2024-38226, and CVE-2024-43491). Seven of the vulnerabilities are rated as Critical in severity, while the remaining 72 vulnerabilities are rated as Important or Moderate.
Risk Analysis September 2024
The top risk type this month is escalation of privilege (38%), followed by remote code execution (29%) and information disclosure (14%).
Figure 1. Breakdown of vulnerabilities found in September 2024 Patch Tuesday by attack technique
Windows products received the most patches this month with 46, followed by Extended Security Updates (ESU) with 23 and Microsoft SQL Server with 13.
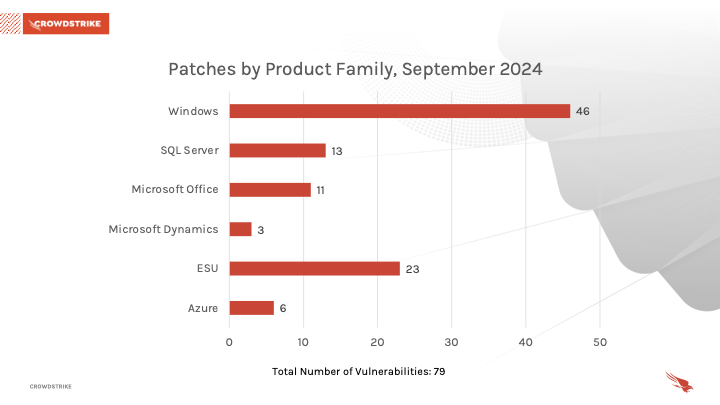
Figure 2. Breakdown of product families affected by the Tuesday correction for September 2024
Zero-Day Vulnerability Actively Exploited in Microsoft Windows Update
Microsoft Windows Update has received a patch for CVE-2024-43491, which has a severity of Critical and CVSS score of 9.8. Microsoft has identified a remote code execution (RCE) vulnerability in the service pack that reverses previously implemented fixes and mitigations, effectively rolling back previous security patches. This vulnerability allows attackers to exploit these previously mitigated vulnerabilities on Windows 10 version 1507 systems that have installed Windows Security Update KB5035858 or other updates released through August 2024. Newer versions of Windows 10 are not affected by this vulnerability. The issue only affects Windows 10 Enterprise 2015 LTSB and Windows 10 IoT Enterprise 2015 LTSB.
CVSS CVE Severity Description
Very important
9.8 CVE-2024-43491 Remote Code Execution Vulnerability in Microsoft Windows Update
Table 1. Zero-day vulnerability in Microsoft Windows Update
Actively exploited zero-day vulnerabilities in Windows Installer
Windows Installer has received a patch for vulnerability CVE-2024-38014, with a severity rating of “Important” and CVSS score of 7.8. An attacker exploiting this vulnerability could gain system-level privileges, potentially allowing them to take full control of the affected system. According to Microsoft, a proof-of-concept toolkit for exploiting the vulnerability is not yet publicly available.
CVSS CVE Severity Description
important
7.8 CVE-2024-38193 Elevation of Privilege Vulnerability in Windows Installer
Table 2. Zero-day vulnerability in Windows installer
Actively exploited zero-day vulnerabilities in Windows Publisher
Windows Publisher has received a patch for CVE-2024-38226, with a severity rating of “Important” and a CVSS score of 7.3. An authenticated attacker could exploit this vulnerability by tricking a web visitor into downloading and opening a specially crafted file from a website. If successful, the attacker could then bypass Office macro policies designed to block untrusted or malicious files. This local attack would require social engineering to convince the victim to interact with the malicious file on their computer, potentially compromising the security of the system.
CVSS CVE Severity Description
important
7.3 CVE-2024-38226 Microsoft Publisher Security Feature Bypass Vulnerability
Table 3. Zero Day in Microsoft Publisher Security
Actively exploited zero-day vulnerability in Windows Mark of the Web
The Windows Mark of the Web (MOTW) tool, a tool that evaluates the security of files downloaded from the web, has received a patch for CVE-2024-38217, which has a severity of “Important” and a CVSS score of 5.4. An attacker could create a file that bypasses MOTW defenses on an end-user system, potentially disabling SmartScreen and Windows Attachment Services security features. This could compromise system integrity and reduce the effectiveness of these safeguards. This security feature has been bypassed multiple times over the years (March 2023, July 2023, November 2023, February 2024, August 2024), making it a prime target for threat actors who use it in phishing attacks. According to Microsoft, a proof-of-concept exploit kit for the vulnerability is not yet publicly available.
CVSS CVE Severity Description
important
5.4 CVE-2024-38217 Web Tag Security Feature Bypass Vulnerability in Windows
Table 4. Day Zero in Windows Web Tag
Critical Vulnerabilities in Windows, SharePoint, and Azure
CVE-2024-43491 is a critical remote code execution (RCE) vulnerability affecting Windows Update with a CVSS score of 9.8. Successful exploitation of this vulnerability allows an attacker to execute arbitrary code remotely. Details are covered in the “Actively exploited zero-day vulnerability in Microsoft Windows Update” section above.
CVE-2024-38220 is a critical RCE vulnerability affecting Azure Stack Hub and has a CVSS score of 9.0. This vulnerability could allow an attacker to gain unauthorized access to applications and content of other Azure cloud tenants. A successful exploit could grant the attacker access to system resources with the same privileges as the compromised process, potentially allowing deeper system compromise and unauthorized actions over the network. To exploit this vulnerability, an authenticated attacker would need to wait for a victim user to initiate a connection to that Azure cloud tenant.
CVE-2024-38018 is a critical RCE vulnerability affecting Microsoft SharePoint Server and has a CVSS score of 8.8. An authenticated attacker with at least site member-level permissions could remotely execute code on SharePoint Server via a network-based attack. According to Microsoft, a proof-of-concept exploit kit for the vulnerability is not yet publicly available.
CVE-2024-38194 is a critical RCE vulnerability affecting Azure Web Apps and has a CVSS score of 8.4. A malicious attacker with valid credentials could leverage an authorization flaw in Azure Web Apps to gain elevated permissions over the network. Microsoft has already fully addressed this vulnerability within the Azure infrastructure, and users of the affected service do not need to take any action. This CVE is being published only to maintain transparency around the issue and its resolution.
CVE-2024-38216 is a critical RCE vulnerability affecting Azure Stack Hub with a CVSS score of 8.2. To exploit this vulnerability, an authenticated attacker would have to wait for the victim user to establish a connection. Once successful, the attacker could gain unauthorized access to system resources, potentially executing actions with privileges consistent with the compromised process. This exploit could lead to further system intrusion, unauthorized network activity, and even the ability to interact with other tenants’ applications and content.
CVE-2024-38119 is a critical privilege escalation vulnerability affecting Network Address Translation (NAT) in Windows with a CVSS score of 7.5. Exploiting this vulnerability requires an attacker to initially breach a protected network perimeter. Additionally, the attacker would need to successfully win a race against the normal execution flow of the program or system to complete the exploit. These requirements add layers of complexity to the attack, which could limit its feasibility. As of now, Microsoft has stated that a proof of concept is not yet available.
CVE-2024-43464 is a critical escalation of privilege vulnerability affecting Microsoft SharePoint Server with CVSS score of 7.2. An attacker with Site Owner privileges or higher could exploit this vulnerability by uploading a maliciously crafted file to a targeted SharePoint Server and sending specially crafted API requests to the targeted SharePoint Server. This process deserializes the file parameters, allowing the attacker to inject and execute arbitrary code on the SharePoint Server, effectively resulting in remote code execution. As of now, Microsoft has stated that a proof of concept is not yet available.
CVSS CVE Severity Description
Very important
9.8 CVE-2024-43491 Remote Code Execution Vulnerability in Microsoft Windows Update
Very important
9.0 CVE-2024-38220 Elevation of Privilege Vulnerability in Azure Stack Hub
Very important
8.8 CVE-2024-38018 Remote Code Execution Vulnerability in Microsoft SharePoint Server
Very important
8.4 CVE-2024-38194 Elevation of Privilege Vulnerability in Azure Web Apps
Very important
8.2 CVE-2024-38216 Azure Stack Hub Elevation of Privilege vulnerability
Very important
7.5 CVE-2024-38119 Remote code execution vulnerability in Windows Network Address Translation (NAT)
Very important
7.2 CVE-2024-43464 Remote Code Execution Vulnerability in Microsoft SharePoint Server
Table 5. Critical vulnerabilities in Windows, SharePoint, and Azure
Falcon Corrective Tuesday Dashboard
For a visual overview of the systems affected by this month’s vulnerabilities, you can use the newly available Patch Tuesday dashboard. It can be found in the CrowdStrike Falcon® platform under Exposure Management > Vulnerability Management > Dashboards. The pre-built dashboards display Patch Tuesday vulnerabilities from the last three months.
Not all relevant vulnerabilities have patches: Consider mitigation strategies.
As we've learned from other high-profile vulnerabilities, such as Log4j, not every exploitable vulnerability is easy to patch. As with the ProxyNotShell vulnerability, it's important to develop a response plan for how to defend your environments when there is no protocol for patching vulnerabilities.
Regular review of your patching strategy should remain part of your program, but you should also take a more comprehensive look at your organization's cybersecurity approaches and improve your overall security posture.
The CrowdStrike Falcon® platform regularly collects and analyzes trillions of endpoint events per day from millions of sensors across 176 countries. Watch this demo to see Falcon in action.
learn more
Learn more about how CrowdStrike Falcon® Exposure Management helps you quickly and easily discover and prioritize vulnerabilities and other types of exposures here.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard used by CrowdStrike and many other cybersecurity organizations to assess and communicate the severity and characteristics of software vulnerabilities. The CVSS base score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a CVSS severity rating. Learn more about vulnerability scoring in this article.
Additional Resources
For more information about products covered by the Microsoft Extended Security Update Program, see vendor guidance here. Learn how Falcon Exposure Management helps you discover and manage vulnerabilities and other exposures in your environments. Learn how CrowdStrike’s external attack surface module, CrowdStrike® Falcon Surface™, detects unknown, exposed, and vulnerable internet-facing assets, enabling security teams to stop adversaries in their tracks. Make prioritization easy and efficient. See how CrowdStrike Falcon® Spotlight empowers IT staff to improve visibility with custom filters and team dashboards. Experience CrowdStrike’s next-generation antivirus for yourself with a free trial of CrowdStrike® Falcon Prevent™.



