Microsoft has released security updates for 51 vulnerabilities in its June 2024 Patch Tuesday release. These patches address one previously disclosed vulnerability affecting the DNS protocol (CVE-2023-50868) and one Very important A vulnerability (CVE-2024-30080) affects Microsoft Message Queuing (MSMQ).
Risk Analysis for June 2024
The leading risk type this month is Lift privilege (49%) followed by Remote code execution (35%) Denial of service (10%) and Disclosure of information (6%)
Figure 1. Breakdown of Corrective Tuesday attack types for June 2024
Microsoft Windows received the most patches this month with 33, followed by the Extended Security Update (ESU) with 23.
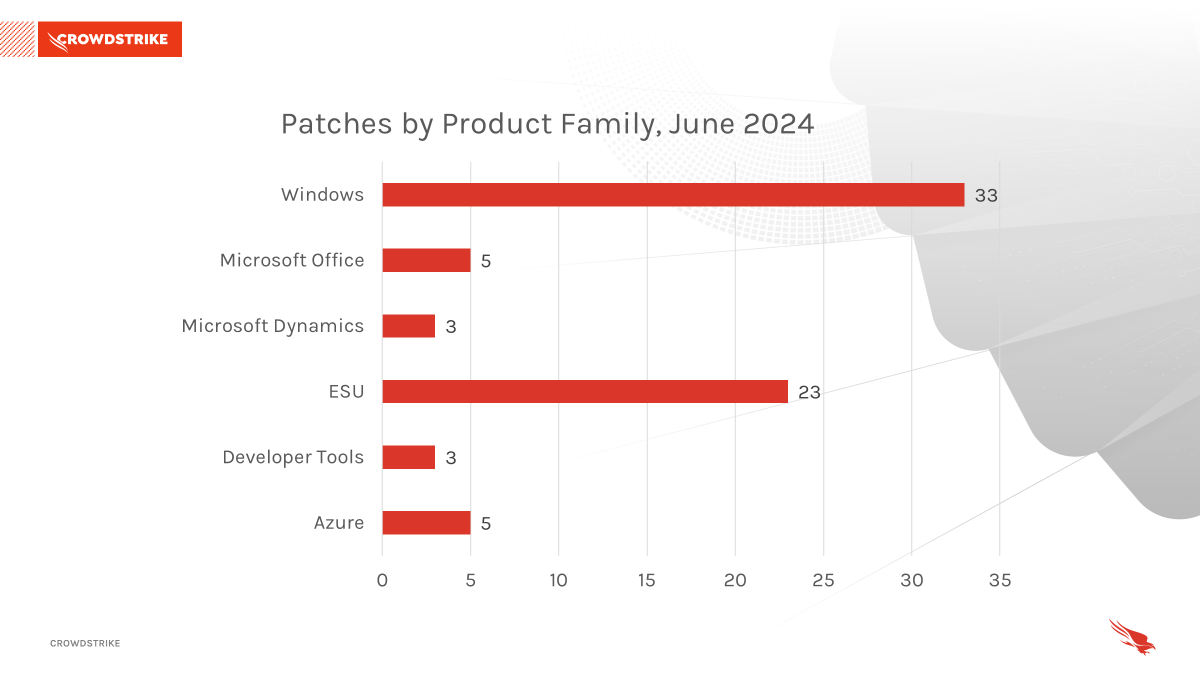
Figure 2. Breakdown of product families affected by the Tuesday correction for June 2024
Zero-Day vulnerability affecting DNS protocol has been patched
CV-2023-50868a denial of service (DoS) vulnerability affecting the DNS protocol with a severity rating of Important And a CVSS Result from 7.5, It is a previously disclosed vulnerability that was fixed in this month's update. The denial of service condition can flood the targeted website or service until it crashes, preventing access for legitimate users.
CVSS CVE Severity Description
Important
7.5 CVE-2023-50868 DNS Protocol — Denial of Service Vulnerability
Table 1. Zero-day vulnerability in DNS protocol
Critical Vulnerability Affects Microsoft's Messaging Service
CV-2024-30080 he Very important Remote code execution (RCI) A security vulnerability affecting the Microsoft Message Queuing service has been identified and has been CVSS Result from 9.8The Windows Message Queuing Service must be enabled, and network traffic must be allowed on TCP port 1801, for an attacker to successfully exploit this vulnerability on a targeted system. An attacker does not need to be authenticated to take advantage of this vulnerability. In addition to its low attack sophistication, this vulnerability poses a particularly serious problem. Successful exploitation could allow an attacker to execute arbitrary code on the MSMQ server. Microsoft urges customers to check whether they are vulnerable by examining whether the named service is Message queue It is enabled and listening on TCP port 1801 on the device.
CVSS CVE Severity Description
Very important
9.8 CVE-2024-30080 Remote code execution vulnerability in Microsoft Message Queuing Service
Table 2. Critical vulnerabilities in MSMQ
Not all relevant vulnerabilities have patches: Consider mitigation strategies.
As we have learned from other notable vulnerabilities, such as: Record4GNot all exploitable vulnerabilities can be easily fixed. As is the case with Notshell Proxy Security vulnerabilities It is very important to develop a response plan for how to defend your environments when there is no patching protocol.
Regular review of your patching strategy should remain part of your program, but you should also take a more comprehensive look at your organization's cybersecurity approaches and improve your overall security posture.
The CrowdStrike Falcon® platform regularly collects and analyzes trillions of endpoint events per day from millions of sensors across 176 countries. Watch this demo to see Falcon in action.
learn more
Learn more about how CrowdStrike Falcon® Exposure Management helps you quickly and easily discover and prioritize vulnerabilities and other types of exposures here.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard used by CrowdStrike and many other cybersecurity organizations to assess and communicate the severity and characteristics of software vulnerabilities. The CVSS base score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a CVSS severity rating. Learn more about vulnerability scoring in this article.



