Microsoft has released security updates for 142 vulnerabilities in its July 2024 patch package. These include two vulnerabilities (CVE-2024-38080 and CVE-2024-38112) that are actively exploited. Five of these vulnerabilities are rated as critical, while the remaining 137 vulnerabilities are rated as critical or moderate.
Risk Analysis July 2024
The top risk type this month is remote code execution (42%), followed by escalation of privileges (18%) and bypass of security features (17%).
Figure 1. Breakdown of Corrective Tuesday attack types for July 2024
Windows products received the most patches this month with 87, followed by Extended Security Updates (ESU) with 67 and SQL Server with 38.
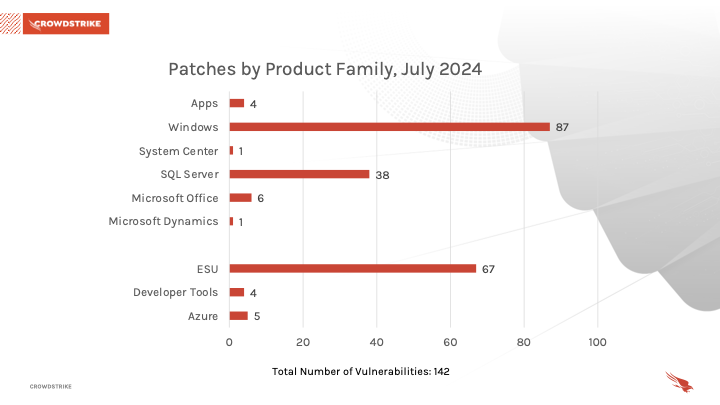
Figure 2. Breakdown of product families affected by the Tuesday correction for July 2024
Actively exploited Zero-Day vulnerability in Windows Hyper-V
Windows Hyper-V has received a patch for CVE-2024-38080, which has a severity of “Important” and a CVSS score of 7.8. This privilege escalation vulnerability allows attackers using low-level authentication to elevate access to gain system privileges. Details of the vulnerability, including a proof-of-concept exploit, have not been publicly disclosed by Microsoft.
CVSS CVE Severity Description
Important
7.8 CVE-2024-38080 Elevation of Privilege Vulnerability in Windows Hyper-V
Table 1. Day Zero in Windows Hyper-V
Actively exploited vulnerability affecting MSHTML platform in Windows
The Windows MSHTML platform has received a patch for CVE-2024-38112, which has a severity of “Important” and a CVSS score of 7.5. This spoofing vulnerability in the Windows MSHTML platform, which is used in all Microsoft 365 and Microsoft Office products, could lead to partial data exposure. An attacker would need to take certain prior actions in order to successfully exploit the vulnerability. Microsoft has not shared details on how exactly the vulnerability could be exploited due to its exploit status. The patch should be applied immediately. Please note that MSHTML had another zero-day associated with it earlier this year (CVE-2024-30040).
CVSS CVE Severity Description
Important
7.5 CVE-2024-38112 MSHTML Platform Impersonation Vulnerability in Windows
Table 2. Day Zero in MSHTML Platform for Windows
Critical vulnerabilities affecting Microsoft Windows Remote Desktop Licensing Service, Windows Imaging component, and Microsoft SharePoint Server
CVE-2024-38074, CVE-2024-38076, and CVE-2024-38077 are critical vulnerabilities affecting Windows Remote Desktop Licensing Services — all with a CVSS score of 9.8. Any of these vulnerabilities could allow an unauthenticated attacker to connect to the Remote Desktop Licensing Service and send specially crafted network packets that could allow remote code execution. Fixes should be prioritized even if the service is disabled.
CVE-2024-38060 is a critical RCE vulnerability affecting the Windows Imaging Component and has a CVSS score of 8.8. Successful exploitation of this vulnerability allows an authenticated attacker to upload a maliciously marked image format (TIFF) file to a server, potentially leading to remote code execution.
CVE-2024-38023 is a critical RCE vulnerability affecting Microsoft SharePoint Server and has a CVSS score of 7.2. An authenticated attacker with Site Owner or higher permissions on a SharePoint site could exploit the vulnerability to execute arbitrary code on the SharePoint server, potentially affecting other sites.
CVSS CVE Severity Description
Very important
9.8 CVE-2024-38074 Remote code execution vulnerability in Windows Remote Desktop Licensing Service
Very important
9.8 CVE-2024-38076 Remote code execution vulnerability in Windows Remote Desktop Licensing Service
Very important
9.8 CVE-2024-38077 Remote code execution vulnerability in Windows Remote Desktop Licensing Service
Very important
8.8 CVE-2024-38060 Remote code execution vulnerability in the Windows Imaging component
Very important
7.2 CVE-2024-38023 Remote Code Execution Vulnerability in Microsoft SharePoint Server
Table 3. Critical vulnerabilities in Windows Remote Desktop Licensing, Windows Imaging Component, and Microsoft SharePoint Server
Vulnerabilities in current proof of concept affecting .NET, Visual Studio, and ARM based operating systems
CVE-2024-35264 is a critical RCE vulnerability affecting .NET and Visual Studio and has a CVSS score of 8.1. Successful exploitation of this vulnerability requires an attacker to win a race condition (two or more threads/processes accessing the same resource) by closing the http/3 stream while processing the request body. Microsoft has not shared further details about the vulnerability.
CVE-2024-37985 is a critical information disclosure vulnerability affecting all ARM-based operating systems and has a CVSS score of 5.9. Successful exploitation of this vulnerability allows an attacker to view the cache (a reserved area within memory to store data) from a privileged process running on the server. An attacker must meet additional pre-exploitation conditions in order to successfully exploit this vulnerability.
CVSS CVE Severity Description
Important
8.1 CVE-2024-35264 Remote Code Execution Vulnerability in .NET and Visual Studio
Important
5.9 CVE-2024-37985 Systematic definition and characterization of prefetch devices
Table 4. Vulnerabilities for which proof of concept is available in .NET, Visual Studio, and ARM-based operating systems
The Importance of Prioritizing SQL Server Debugging
Thirty-eight of the vulnerabilities this month affect SQL Servers. Given the importance of SQL Servers and the challenges associated with patching these critical servers, we strongly recommend prioritizing SQL-related patches due to the time often required for testing and rollback.
Not all relevant vulnerabilities have patches: Consider mitigation strategies.
As we've learned from other high-profile vulnerabilities, such as Log4j, not every exploitable vulnerability is easy to patch. As with the ProxyNotShell vulnerability, it's important to develop a response plan for how to defend your environments when there is no protocol for patching vulnerabilities.
Regular review of your patching strategy should remain part of your program, but you should also take a more comprehensive look at your organization's cybersecurity approaches and improve your overall security posture.
The CrowdStrike Falcon® platform regularly collects and analyzes trillions of endpoint events per day from millions of sensors across 176 countries. Watch this demo to see Falcon in action.
learn more
Learn more about how CrowdStrike Falcon® Exposure Management helps you quickly and easily discover and prioritize vulnerabilities and other types of exposures here.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard used by CrowdStrike and many other cybersecurity organizations to assess and communicate the severity and characteristics of software vulnerabilities. The CVSS base score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a CVSS severity rating. Learn more about vulnerability scoring in this article.
Additional Resources
For more information about products in the Microsoft Extended Security Update Program, see vendor guidance here. Read the CrowdStrike 2024 Global Threat Report to learn how the threat landscape has transformed and understand the adversary behavior driving these shifts. See how Falcon Exposure Management can help you discover and manage vulnerabilities and other exposures in your environments. Learn how CrowdStrike’s external attack surface module, CrowdStrike® Falcon Surface™, detects unknown, exposed, and vulnerable internet-facing assets, enabling security teams to stop adversaries in their tracks. Make prioritization easy and effective. See how CrowdStrike Falcon® Spotlight empowers IT to improve visibility with custom filters and team dashboards. Experience CrowdStrike’s next-generation antivirus for yourself with a free trial of CrowdStrike® Falcon Prevent™.



