Almost every week we add another workflow to our automation library. Our Copilot platform helps people automate tedious tasks in security operations. Cross-platform integrations traditionally involve security engineers writing custom code using application programming interfaces (APIs).
For example, if you want to scan all your S3 buckets for public access, look for read and write permissions, and send a notification to a Slack channel for incident response, you'll need Python or Bash code with several API calls.
However, with security automation platforms like Blink Ops, this has changed radically. You can integrate automation into your environment by typing a simple prompt, and Copilot will build the workflow it thinks you need. It's then a matter of entering some parameters and adding authentication credentials. This can save people in security operations hundreds of hours per year.
Here's a list of five incident response/security workflows you can automate with Blink Ops. These examples give you an idea of how Blink Ops automations can speed up your business.
1. Monitor subdomain hijacking using AWS and Wiz
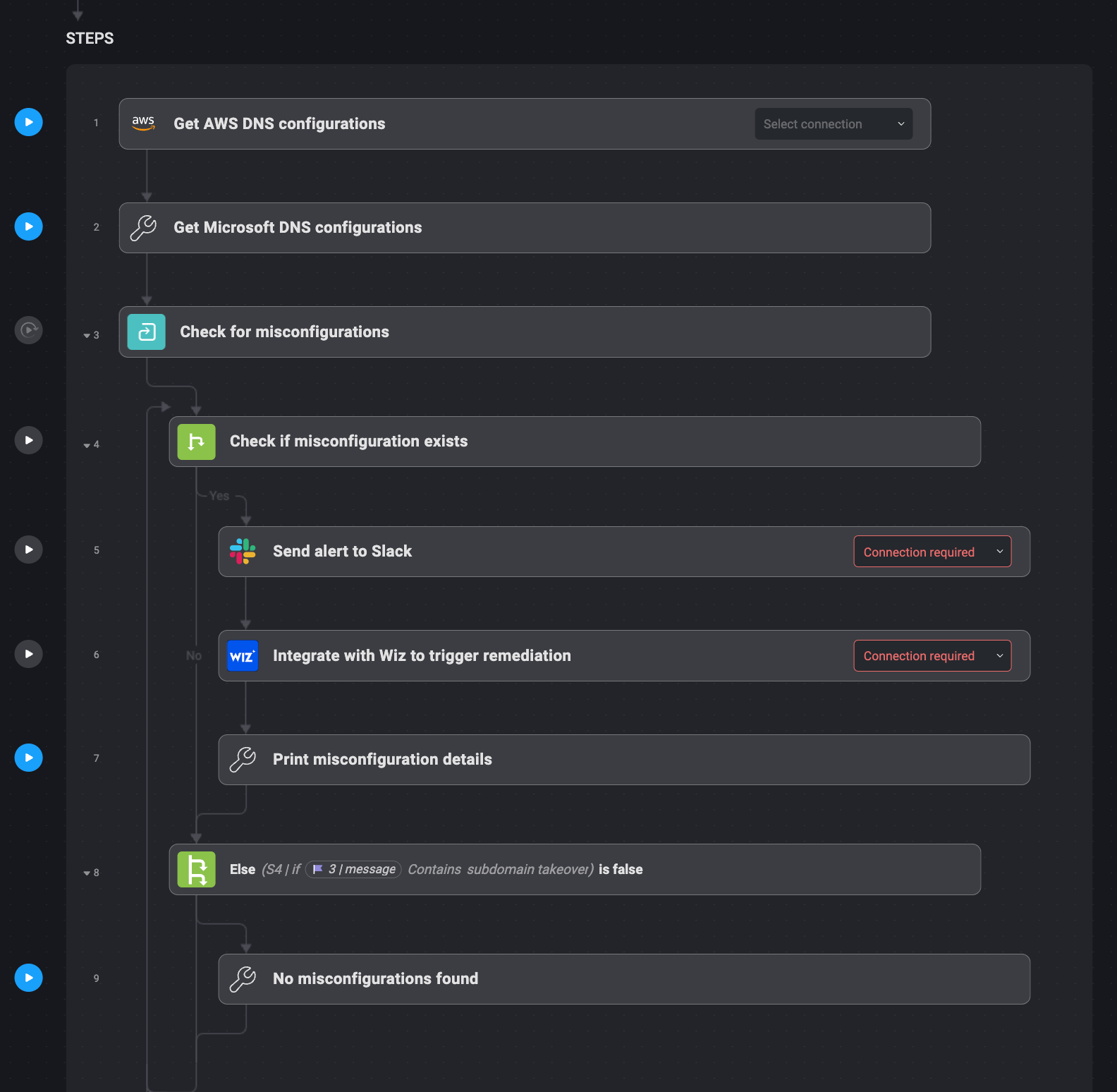
Subdomain hijacking occurs when a DNS entry points to a resource that does not exist or is inactive, allowing attackers to hijack the domain. Trying to prevent this manually involves frequent checks to make sure all DNS configurations are correct.
This process is fully automated using Blink Ops. In conjunction with AWS Route 53, Blink Ops scans for orphaned/pending CNAME records that point to resources that no longer exist using Wiz. When issues are detected, Blink Ops sends an immediate alert to a specific Slack channel describing a misconfigured DNS entry.
Wiz then quarantines the registry or takes repair steps. When no issues are found, a notification is sent that everything is secure. This automation simplifies detecting and mitigating subdomain hijack risks.
Bullet point steps:
1. For DNS configurations, Blink Ops connects to AWS Route 53.
2. Wiz checks DNS entries for orphaned CNAME records.
3. When a vulnerable record is found, Blink Ops sends an alert to Slack.
4. Wiz either quarantines the registry or applies the repair.
5. If no issues are found, a confirmation email will be sent confirming this.
2. Monitor exposed S3 buckets with stagnation alerts
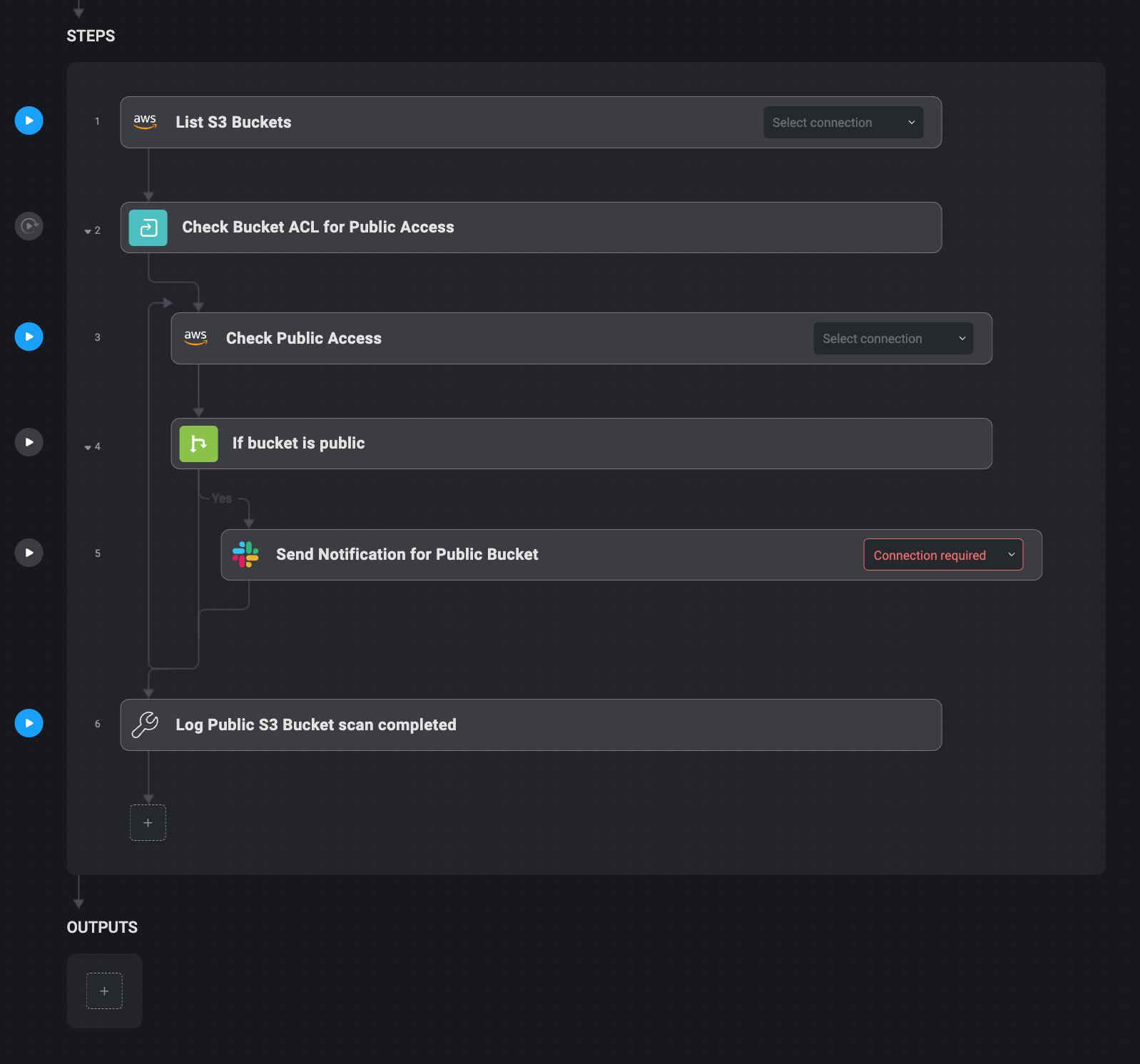
Exposed S3 buckets represent a significant security risk for any organization, and tracking them manually every day can be daunting. You can address this issue by enabling daily automatic scans for S3 buckets with global read permissions.
This workflow integrates with AWS S3, and Blink Ops can inspect every bucket that is marked for public access. Detecting a container with public read access triggers a Slack alert from Blink Ops, providing the security team with information about the container — including its name and permissions.
The follow-up action performed by Blink Ops can also remove the public permission of the container. This workflow identifies exposed containers quickly and appropriately so that sensitive data is not exposed to unauthorized users.
Bullet point steps:
1. Blink Ops daily checks AWS S3 buckets for global read permissions.
2. Any container found with public read access triggers a Slack alert.
3. Blink Ops can optionally revoke read permissions (note – not listed above).
4. The bucket is secured and the security team is informed.
3. Respond to failed EC2 logins and privilege escalation
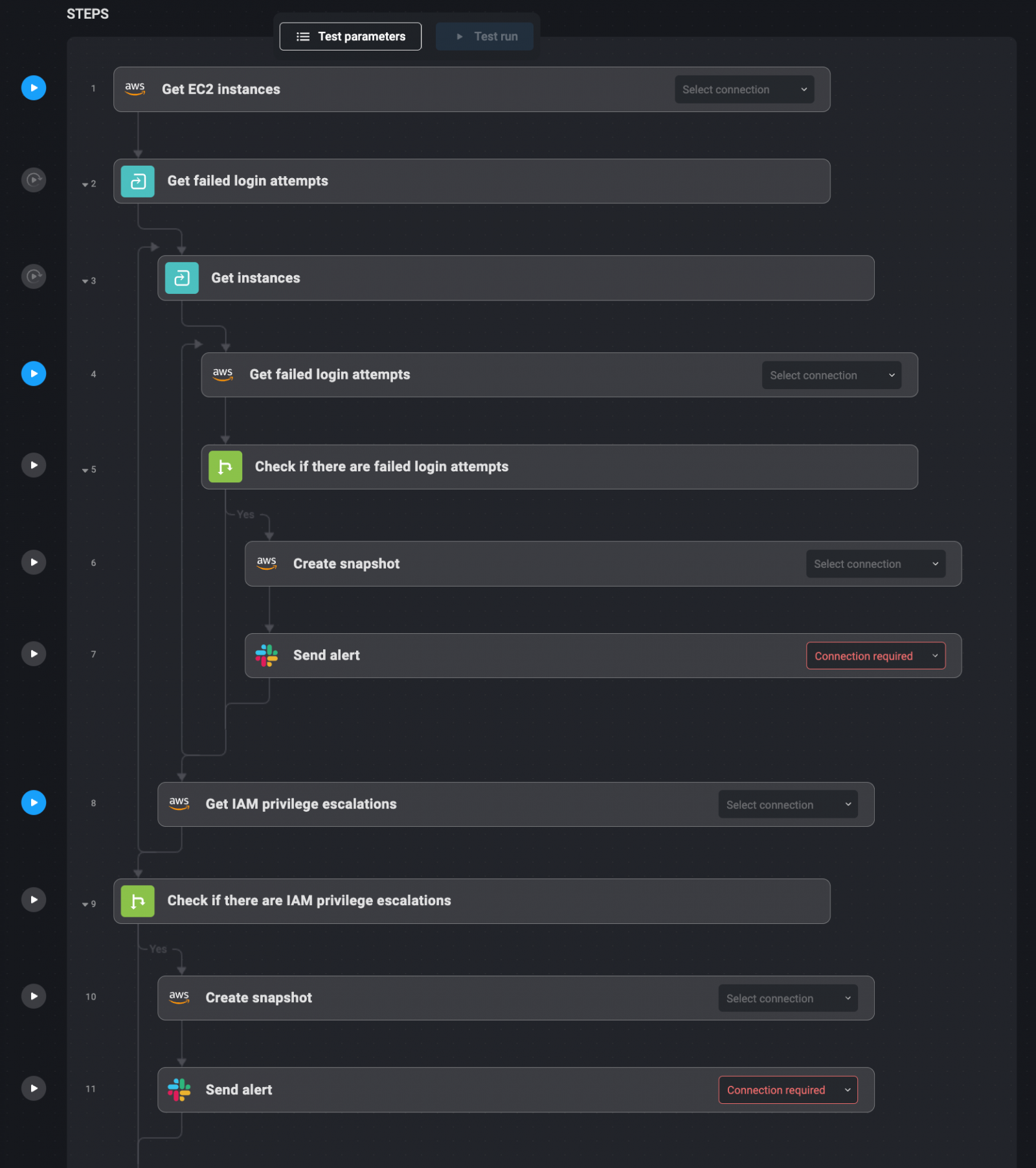
Failed login attempts and detecting and responding to unauthorized privilege escalation on EC2 instances is critical to security. Blink Ops can automate this so that threats are detected and responded to in real time.
You can monitor EC2 instances to detect frequent failed login attempts via SSH or RDP – five or more failed attempts in a 15-minute window – via Slack. You can also track privilege escalation by monitoring IAM role changes, such as when an EC2 instance is granted additional privileges such as AdminAccess.
When this happens, Blink Ops takes a snapshot of the affected EC2 instance for forensic analysis and sends an alert to the security team describing what happened. This automation relieves security teams from manually monitoring the log during login failures or abuse of privileges.
Bullet point steps:
1. Failed SSH and RDP login attempts on EC2 instances are tracked by Blink Ops.
2. If more than 5 failed logins occur within 15 minutes, Blink Ops issues a Slack alert.
3. IAM role changes, such as privilege escalation, are also tracked by Blink Ops.
4. When privilege escalation occurs, Blink Ops takes a snapshot.
5. Security teams receive alerts that include all details related to the event.
4. Detect and alert on vulnerabilities using AWS Inspector
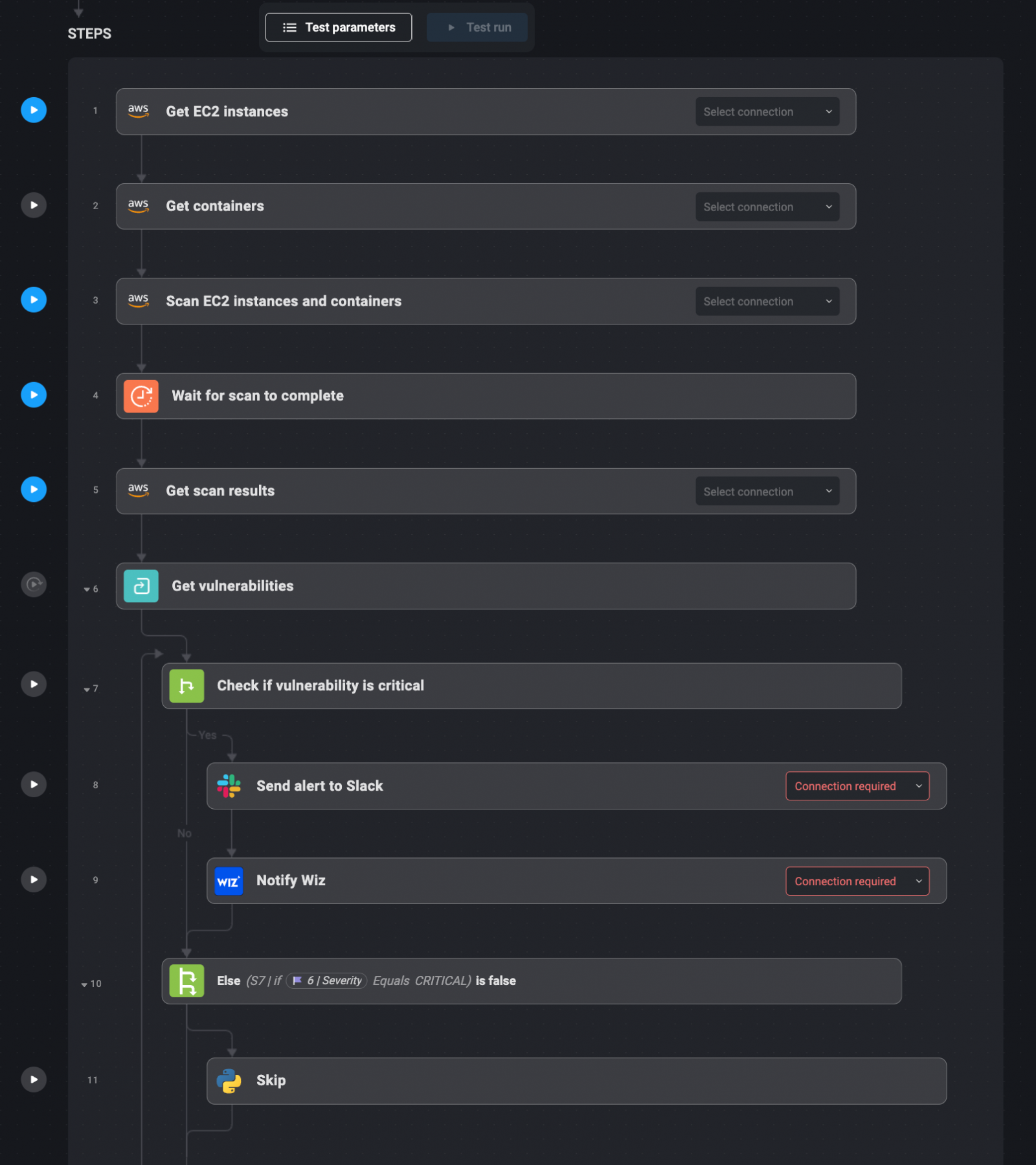
Vulnerability management is essential to keeping cloud environments secure. Blink Ops simplifies the process by integrating with AWS Inspector to automatically scan EC2 instances and containers for critical vulnerabilities.
As part of Blink Ops, AWS Inspector can check for high-risk vulnerabilities such as CVSS scores greater than 7. Once a critical vulnerability is detected, Blink Ops notifies the designated Slack channel of the vulnerable instance/container. The alert is also linked to the treatment manual or operation manual for manual intervention.
For vulnerabilities that cannot be patched automatically, Blink Ops logs the details and allows manual remediation by a security engineer. Once the remediation process is complete, Wiz verifies that the vulnerability has been fixed, ensuring that the cloud environment is secure.
Bullet point steps:
1. AWS Inspector scans EC2 instances and containers for vulnerabilities.
2. When a vulnerability is detected (CVSS >7), Blink Ops sends an alert to Slack.
3. Wiz confirms that the vulnerability has been fixed after manual remediation.
4. Security teams are notified when the repair and verification process is completed.
5. Automate implementation of S3 encryption using AWS and Wiz
Securing sensitive data in S3 buckets is a best practice. This issue is solved by automating S3 bucket monitoring for cryptographic compliance with Blink Ops.
Monitoring of sensitive data sets tagged with S3 via Blink Ops is integrated with AWS Config. It verifies that these buckets are encrypted using AES-256. When an unencrypted bucket is detected, Blink Ops applies AES-256 encryption using AWS's PutBucketEncryption API.
After encryption is applied, Blink Ops sends a confirmation to Slack for the update, and Wiz launches to verify that encryption is applied. This automated workflow protects all sensitive data without any human intervention and enables security teams to enforce encryption policies across the cloud.
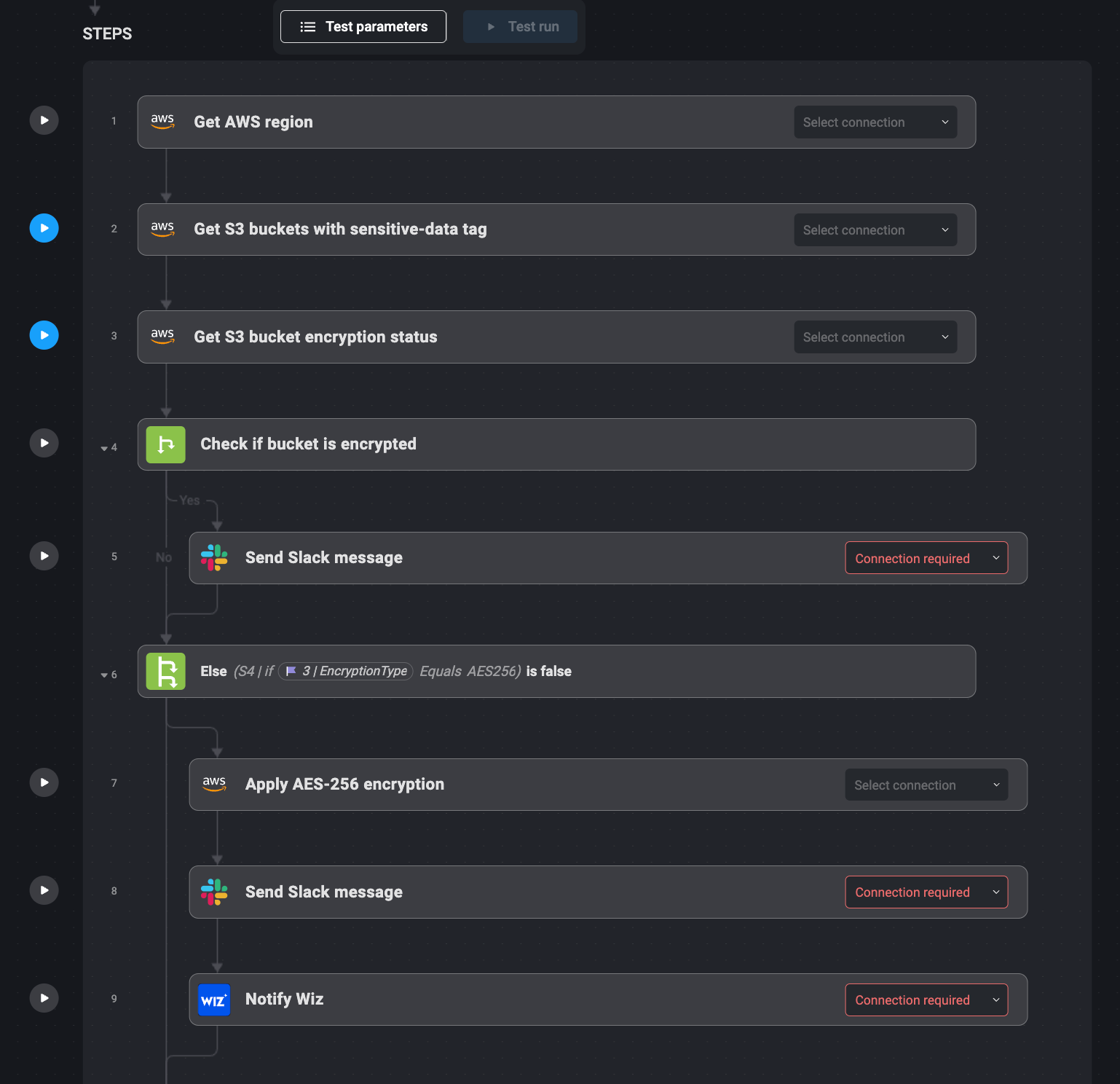
Bullet point steps:
1. AWS Config tracks S3-tagged sensitive data sets monitored by Blink Ops.
2. When not encrypted, Blink Ops runs AWS to implement encryption.
3. When encryption is applied, a Slack notification is sent.
4. Wiz confirms that encryption has been applied correctly.
5. Security teams now know that the bucket is secured.
Take your next steps with Blink Ops
The above use cases are just some of the many possibilities that Blink Ops can automate for you. Blink Ops can be used with platforms like AWS and Wiz to automate processes that used to require custom code and manual work. This means security teams can save man-hours, respond faster to threats, and reduce the risk of human error.
Automate time-consuming tasks so your team can focus on higher-value security initiatives, with Blink Ops. Whether you need to monitor subdomain hijacking, detect failed EC2 logins, or automate vulnerability scans, Blink Ops lets you improve and scale your security operations.
Get started with Blink Ops today to automate repetitive tasks.
Sponsored and written by Blink Ops.



