The failure to audit compliance is still a decisive challenge for institutions, especially in the security of the database. According to the 2024 Thales data threat report, approximately 43 % of companies failed to comply with compliance last year. This is a great concern because the audit failures are closely related to security incidents-organizations that failed in audit operations that were more vulnerable to ten-time data violations, as they have reached 31 % of the organizations that are not compatible with violations, compared to only 3 % between those that followed. This confirms the primary role of compliance in maintaining data security with the development of new threats.
Increasing electronic threats, especially ransom programs and harmful programs, increases pressure on compliance efforts. Human error is a prominent factor, as it contributes to a large part of violations and the complexity of the compliance scene, which requires strong practices of data and security management.
In response, many institutions adopt compliance solutions, which simplifies the audit and reduce safety gaps caused by human oversight. The automated tools of institutions can stay ready to scrutinize and safer, even as regulations change and e -threats increase more sophisticated.
Subscribe to our web symposium on February 27, 2025, and simplifying your safety: automating the compliance database assessments with Ambrys Cloud Agent.
The importance of compliance with the database and challenges
Compliance with the database has become a priority among industries in today's world -based world. With regulations such as GDP, PCI DSS, CIS and HIPAA that impose strict requirements, lack of compliance is risks such as data violations that offer sensitive information, major financial penalties that can affect the stability of the organization, and the damage that undermines the confidence of the stakeholders. Compliance protects sensitive data, builds customer confidence, maintains the organization's reputation, and is increasingly vital with intensification of organizational enforcement. This environment calls for a comprehensive approach to managing a database security, and integrating best practices to maintain data safe and compatible.
Traditional ratification surveying facing great challenges, despite the provision of advantages such as central administration and expansion. The lack of sharing and managing accreditation data safely to access the database increases the risk of unauthorized access, creating possible security gaps.
The network -based scanning can be consumed by the large number of frequency range, which may affect the performance of the system and the network, especially in large environments. The failure and authorization failure is also common, which causes delay and requires repeated attempts to reach resources. These failures can slow the survey and affect the efficiency of the network in general.
Moreover, light scanners may fight a distance to detect problems hidden behind protection walls, VPNS or complex network formations. Together, these factors hold comprehensive management to examine compliance.
The current presentation of the QUALYS Compliance Policy provides a comprehensive coverage of the policy of compliance with databases and provides flexibility through various data collection sensors, such as light scanners and cloud agents.
Although Quals Scanner faces challenges such as challenges associated with the traditional survey of the ratified dimension of them, it addresses many of these problems by providing long -term support for the authentication of the database and its evaluation to comply with politics. Through a wide range of subsidized databases, the QUALYS scanner simplifies the survey process and evaluates database environments, which helps institutions ensure compliance while reducing the effect of performance.
On the contrary, the QUALYS Cloud agent has so far supported the OS level database assessments. Although its scope was more limited than Qales-which focuses mainly on the OS-Auth level control elements for specific database techniques-it provides a flexible and safe method for conducting assessments, even in complex or difficult environments. There is no effect on the network, as it is also suitable for assets that you cannot get its approval data, seeing continuous authentication failure, or having sensitive servers to wipe the port.
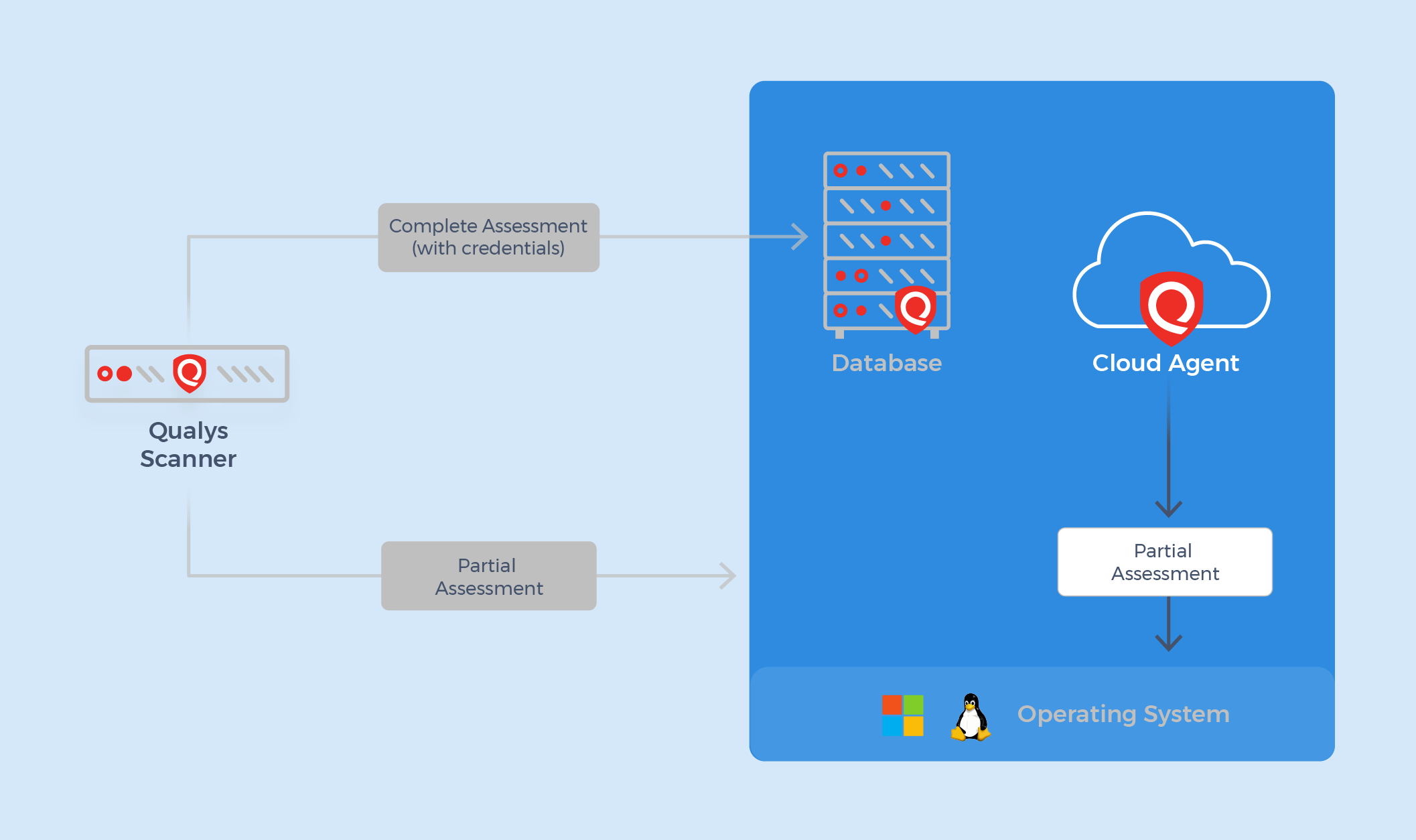
Although the cloud agent was excellent in monitoring, he had previously lacked the ability to make comprehensive database assessments due to his inability to log in to the databases directly.
Provide and evaluate the QUALYS Cloud Agent database
To face these challenges directly, QULYS enhances its capabilities by entering the database assessment feature using the Cloud Cloud agent. This powerful and cloud solution is designed to monitor and evaluate databases continuously to comply with safety policies, providing institutions to the tools you need to stay at the forefront of potential risks. With the support of Oracle and MS SQL databases, the Cloud Cloud agent ensures adherence to many of the Association of Independent Countries, Disa, NIST, and many standard policies, which enhances a strong security situation.
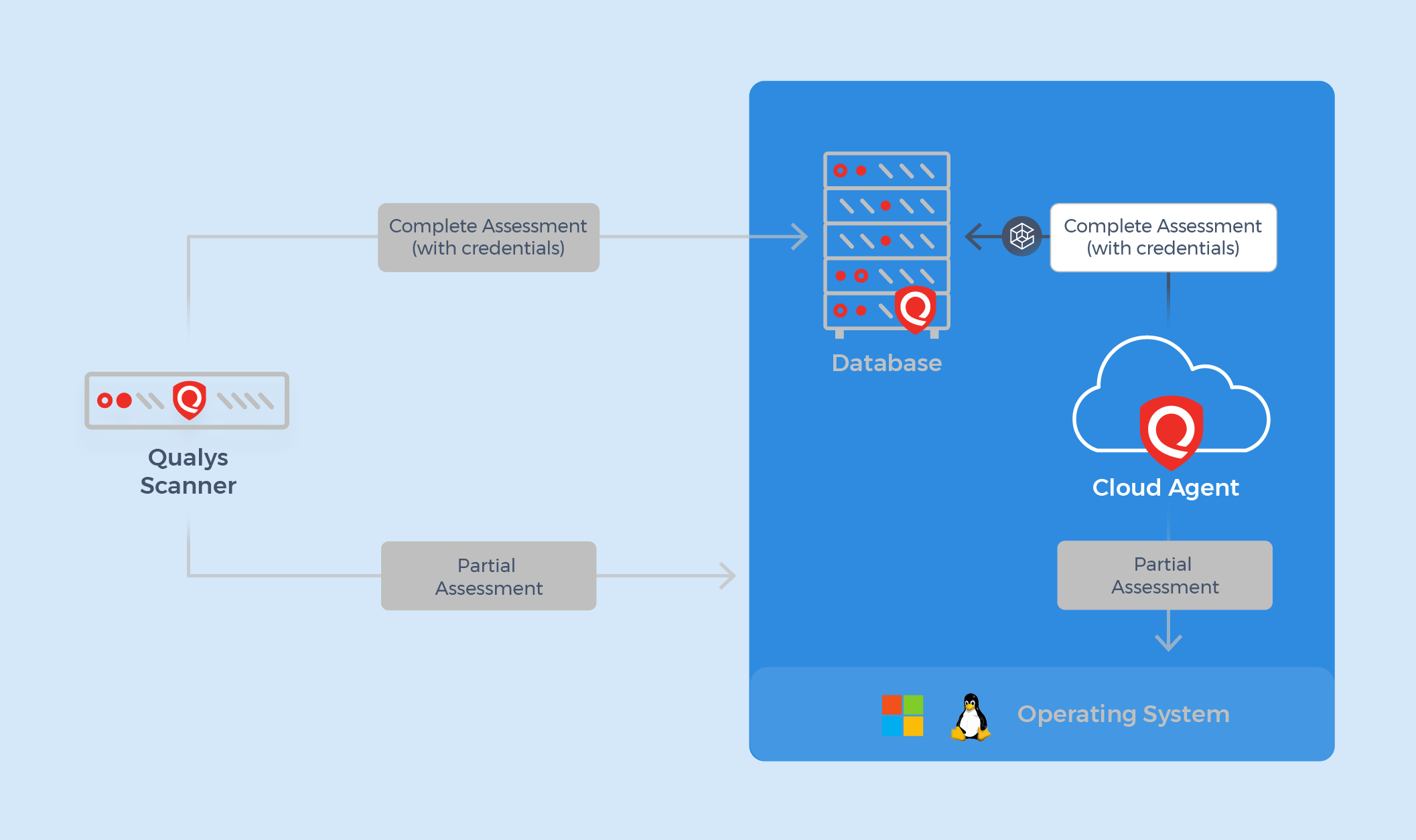
The authentication and evaluation feature of the Cloud Agent database allows safe and mechanical evaluations by contacting the Vauult provider to recover accreditation data and authentication databases. This approach enables institutions to effectively simplify the database security management. This innovative approach not only enhances the general security position of the organization, but also guarantees compliance without the traditionally related public expenditures associated with the database assessment.
The main features of the database assessment
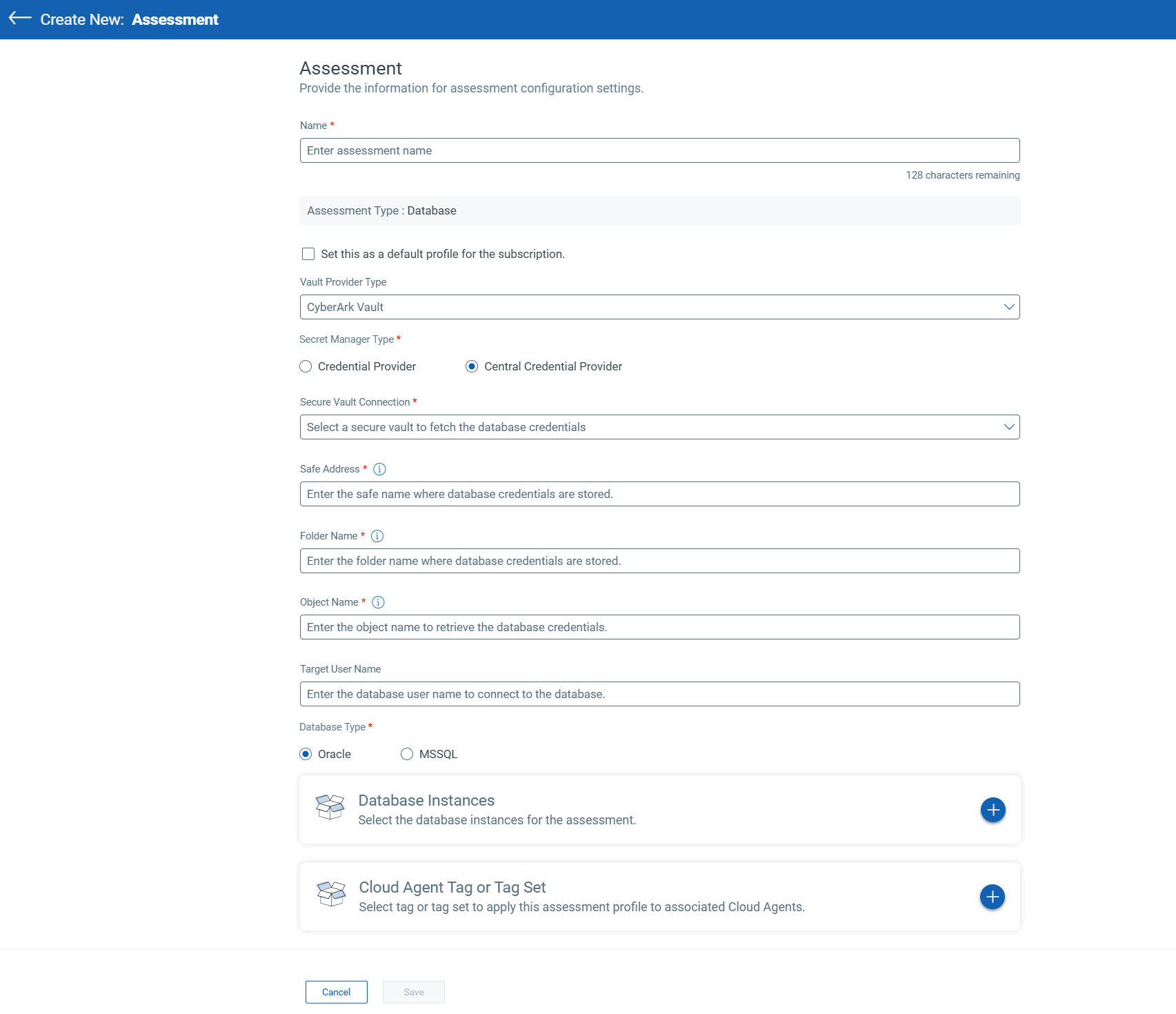
1. Integration Vauult and Secret Manager: Supports integration with Cyberark Vault and different SECRET Manager types (Accreditation Data Provider, Central Approval Data Provider) to manage safe database accreditation.
2. Create a database assessment: The cloud factor directly connects to the Vauult provider (for example, Cyberark Vau) to bring accreditation data safely to the Oracle and SQL database assessments.
3. Evaluation Management: The evaluation tab allows the creation, display and deletion of database assessments, with options to mark and set the definition files.
Benefits of the database assessment feature
1. Organizational compliance: The ability to conduct policy compliance ensures that institutions can meet strict regulations such as GDP, PCI DSS, CIS, ISO and HIPAA, thus relieving costly penalties.
2. The improved compliance status: Determining early formation operations allows institutions to address discrimination operations before their exploitation, and improve public security and compliance. By proactively addressing these issues, companies can reduce the risk of violations, ensure adherence to organizational standards, and avoid the failure of scrutiny and penalties.
3. Comprehensive assessments: The QUALYS cloud agent conducts in -depth reviews of the databases, determining the compliance gaps that may pose risks to the organization.
4. Continuous monitoring: with actual time monitoring capabilities, institutions can remain aware of the security of their database and address any problems in compliance quickly.
5. Automation: The Cloud Cloud agent performs automatic scanning operations, eliminating the need for manual scheduling. This allows institutions to reduce the time and resources necessary for handicrafts, allowing security teams to focus on strategic initiatives instead of routine compliance tasks.
How to start
By April 2025, the feature will be enabled by all accounts that support policy compliance. Until then, customers must contact Qallys support or technical account manager (TAM) to enable the feature.
conclusion
The launch of the QUALYS Cloud agent assessment feature is a great progress in the database safety. By providing institutions with the tools needed to automate compliance tests and monitor their databases constantly, Qalys enable companies to protect their sensitive data more effectively than ever. In an era, violations and organizational penalties can have severe consequences, the ability to ensure compliance and enhance the security position is not only useful – they are necessary for the success of the ongoing business.
With Quales, institutions can mobilize the complications of the database security with confidence, knowing that they have a strong ally in their pursuit of security and security excellence.
Call your Tam and enable today!
The current Quiles customers can contact their technical account manager (TAM) to arrange a experimental show and discuss how this feature is designed to meet their specific needs.



