As modern cyberattacks increasingly target cloud environments, it's essential that organizations have the technology they need to detect and stop them.
The attack surface of cloud-native applications and infrastructure is expanding rapidly. Cloud Native Application Protection Platforms (CNAPPs) meet the growing need for modern cloud security monitoring, security posture management, intrusion prevention and control tools to fully protect cloud environments. The CNAPP market has seen tremendous growth as organizations seek to strengthen their security defenses.
So what is CNAPP, and what possibilities does it include? What vulnerabilities do you solve for security and development teams? What should security leaders look for in a CNAPP? These questions are answered in Gartner®'s 2024 Market Guide for CNAPPs.
Here we share some of the most important takeaways from our new market guide. We highly recommend downloading the full report here.
What is CNAPP?
CNAPP is a security solution designed to protect applications built and running in cloud-native environments. These environments typically include microservices, containers, and dynamic platforms like Kubernetes. CNAPPs provide visibility across cloud infrastructure, workloads, applications, APIs, data, and third-party dependencies. Ultimately, CNAPPs provide security across the entire application lifecycle, from development to deployment and runtime.
Figure 1. This graphic was published by Gartner, Inc. As part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from https://www.gartner.com/doc/reprints?id=1-2IIVY3JL&ct=240815&st=sb.
What problems does CNAPP solve?
The rapid growth of cloud-native applications and multi-cloud environments in enterprises around the world has expanded the attack surface and changed the security landscape. Traditional security tools are no longer sufficient to defend against modern cyber attacks.
Here are some of the recent cybersecurity challenges that CNAPP aims to address:
Secure multi-cloud environments: Unified platforms simplify defense and enhance efficiency by addressing the complexity of multi-cloud security. Visibility gaps for security teams: Comprehensive CNAPPs provide a single view of your cloud environment, eliminating visibility gaps caused by siled tools. High maintenance costs: CNAPPs reduce time and costs by consolidating security tools into a single solution. Slower detection and response: CNAPPs enable real-time detection and response, preventing attackers from moving undetected. Cloud and application misconfigurations: CNAPPs ensure protection by identifying misconfigurations early, from development to production. Friction between development and security: Embed comprehensive security early in the development cycle, preventing threats from impacting runtime operations.
We are pleased to be listed as a representative supplier in the Gartner 2024 Market Guide for CNAPPs. Let's take a closer look at the six key points we took away from this report.
1. CNAPPs need a cloud detection and response (CDR) solution.
According to Gartner, “Prioritizing risk outcomes is critical, as developers and security professionals are overloaded with alerts and siled tool outcomes,” leading to slow response times. Security is not just about detecting threats, it is about understanding them in context and stopping breaches before they happen. Siloed solutions often fail to provide comprehensive protection and context, because they lack the ability to connect disparate events without the need for complex custom integrations. Additionally, there is a notable skills shortage in the cybersecurity industry, including Security Operations Center (SOC) analysts and others involved in detection and response, but who come from a local background.
To reduce response times, organizations need to adopt CDR capabilities that go beyond “…core workload monitoring” to enhance correlation and processing, as stated by Gartner. CDR is a comprehensive security approach designed for cloud environments, including 24/7 Managed Detection and Response (MDR), 24/7 proactive threat hunting, specialized cloud services and unified CNAPP to ensure complete cloud security coverage from prevention to… Detection and even treatment.
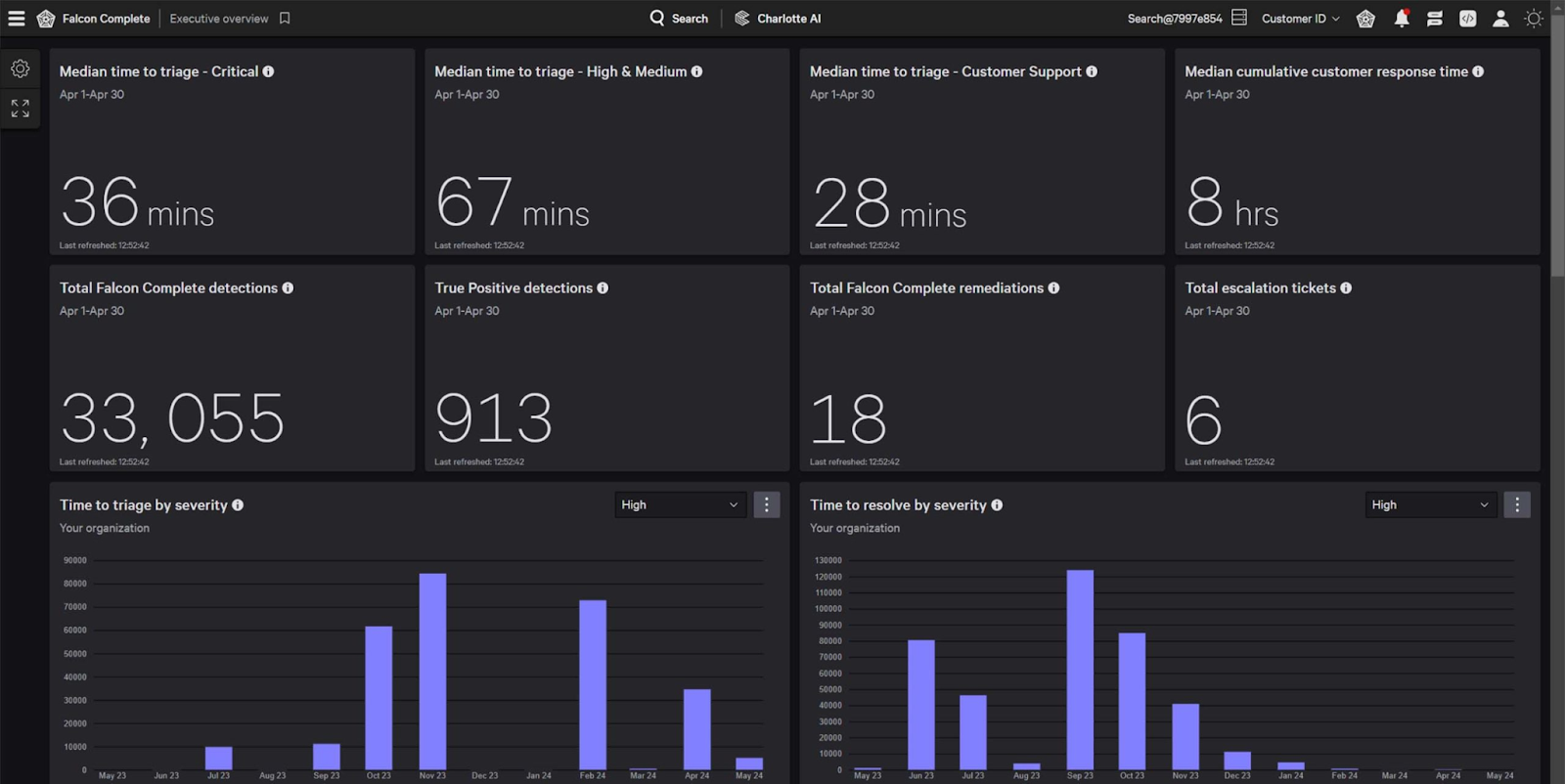
Figure 2. CrowdStrike Falcon® Complete Next-Gen MDR Managed Detection and Response dashboard (calculation performed by CrowdStrike)
2. CNAPPs must prioritize risks through the lens of business context
According to Gartner, “CNAPP tools must be able to model application code, libraries, containers, scripts, configuration, and vulnerabilities to identify where effective risks exist. Because risk-free applications are impossible, information security must prioritize risk outcomes according to the business context, identifying root cause and enable developers to focus first on the most critical outcomes with the highest confidence in the potential business impact.
The pace at which cloud-native applications are built, delivered, and updated makes it essential for organizations to manage risks, not vulnerabilities. Securing everything built and running in the cloud requires different capabilities, including Application Security Posture Management (ASPM), to work together with one overarching goal in mind: managing risk for business impact.
Identifying, assessing, and prioritizing issues based on impact, exploitability, and likelihood across an organization's entire cloud architecture is essential for organizations building cloud-native applications. When CNAPP can correlate and analyze findings so customers can clearly identify which issues create the most risk to the business, addressing those risks becomes a shared goal across security, development, and operations teams.
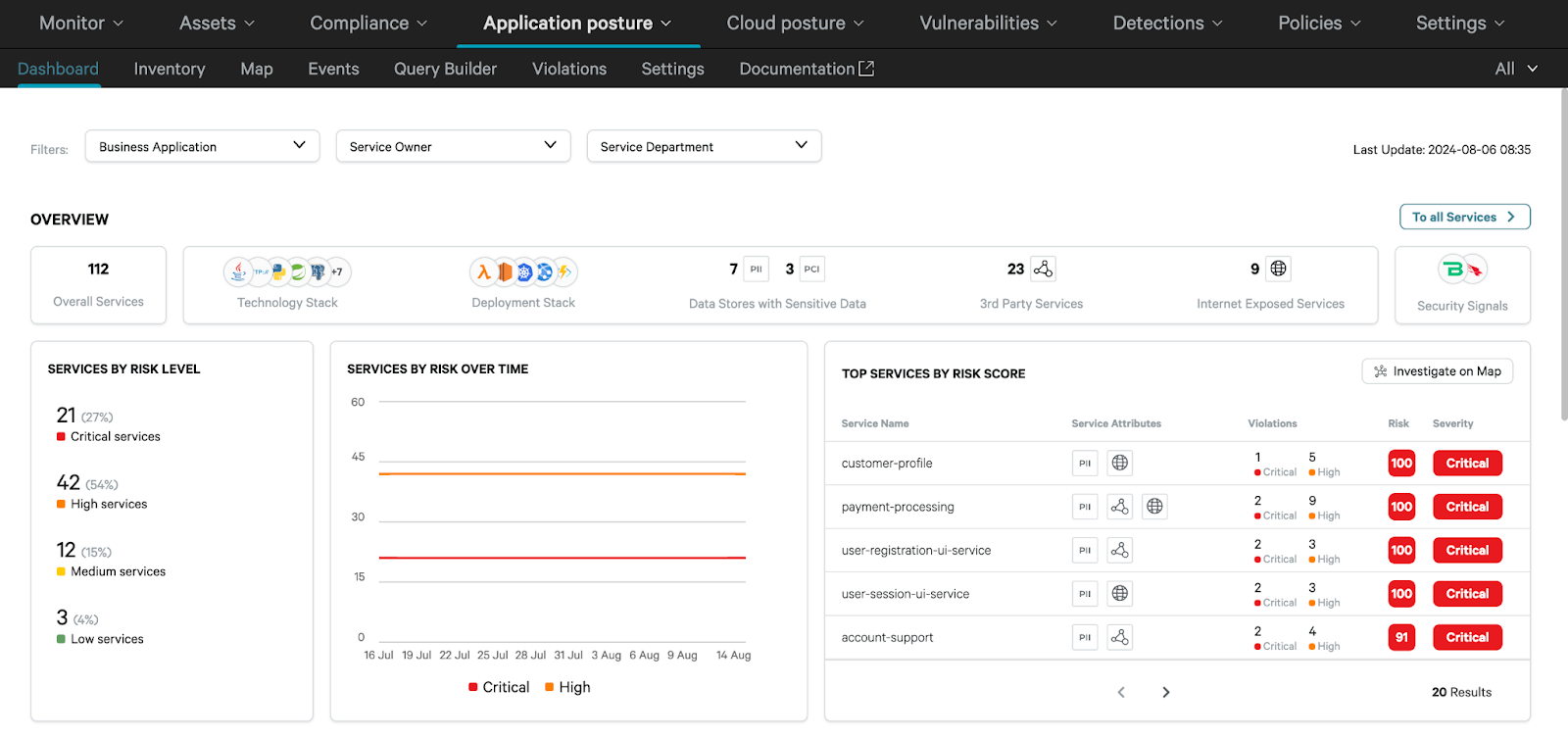
Figure 3. Seeing risk from a business application lens in Falcon Cloud Security (calculations/graphic created by CrowdStrike)
3. CNAPPs must be able to classify sensitive cloud data
Gartner notes that “…understanding the context of data in structured and unstructured repositories is essential to fully understanding, addressing and prioritizing risk context, but many CNAPP vendors do not yet offer this.”
Organizations are focused on securing cloud-native applications and their underlying data throughout the development lifecycle. Comprehensive data security requires monitoring data in use and in motion, allowing you to detect shadow data in unmanaged stores and track data movements to third-party services. Integrating Data Security Posture Management (DSPM) into CNAPP provides comprehensive security coverage, enhances data flow security and improves alert management. By analyzing data across its lifecycle and within a unified cloud security framework, you can achieve robust protection and peace of mind.
4. CNAPPs enable development and security teams to collaborate
“By 2029, 35% of all enterprise applications will run in containers, up from less than 15% in 2023,” says Gartner.
DevSecOps teams are the engine that powers modern application-driven enterprises. They rely on CNAPP tools that provide context and focus for security teams to quickly identify the most critical vulnerabilities and then bring them back to developers to remediate. Alert fatigue is a real problem, as CNAPPs that simply flag everything — without the benefit of rich threat intelligence and experience to help prioritize risks — can dramatically slow down response time and distract from fixing the most serious issues first. This is where tools like Infrastructure as a Code (IaC) workflows, leveraging log-based data, can help flag the right developer in the right context and allow for faster and easier processing. Additionally, security verification is pre-integrated into the CI/CD pipeline using tools such as IaC scanning to verify templates, pre-launch container analysis, and registry scanning, which can allow for more secure pre-deployment of the application and ensure a better end-user experience.
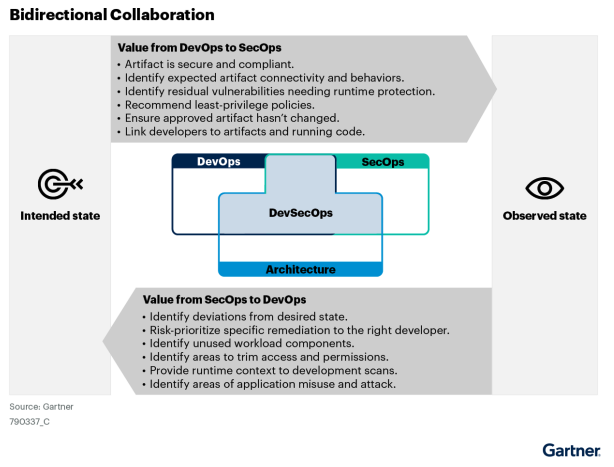
Figure 4. Gartner CNAPP Market Guide, Two-Way Collaboration
This graphic was published by Gartner, Inc. As part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from https://www.gartner.com/doc/reprints?id=1-2IIVY3JL&ct=240815&st=sb.
5. Runtime visibility and analysis is a key part of CNAPP
Gartner notes that CNAPP should have “runtime visibility into workload states, either in real-time or through real-time analysis, to detect vulnerabilities, secrets, and anomalous behaviors in cloud workloads (virtual machines, containers, and serverless).” Use this to add context to your cloud configuration results.”
CNAPP needs to provide continuous, real-time monitoring to identify new and unusual threats. To help with this, you need to leverage adversary-based threat intelligence and AI-powered analytics. CNAPP must also provide a unified view of the complete path an attacker can take, from host to cloud, to compromise the cloud environment.
6. CNAPPs must have a unified view of risk
“By 2029, 60% of organizations that do not deploy a unified CNAPP solution within their cloud architecture will lack broad visibility into the cloud attack surface and will therefore fail to achieve their desired Zero Trust goals,” says Gartner.
Unified CNAPP brings together essential security tools, providing end-to-end visibility and enabling organizations to detect and respond to threats more effectively while maintaining consistent security across all cloud assets. By integrating every aspect of cloud security – Cloud Workload Protection (CWP), Cloud Security Posture Management (CSPM), DSPM, ASPM, Cloud Infrastructure Rights Management (CIEM), Container and Kubernetes Security, IaC, and BOM (SBOM), Compliance and CDR – in one console, providing deep visibility, real-time detection and response across the entire cloud-native stack.
Request a cloud security health scan to assess the security of your cloud environment and detect potential risks.
At CrowdStrike, we believe we stand by these key points from the Gartner report. Falcon Cloud Security heralds a new era of cloud security. Our comprehensive approach ensures your cloud infrastructure, applications and data are protected from all angles, enabling you to stay ahead of emerging threats and maintain a strong security posture.
Gartner, Inc. Market Guide. For cloud-native application protection platforms. Dale Goeben, Charlie Winkless, et al. July 22, 2024.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the United States and internationally, and is used here with permission. All rights reserved.
Gartner does not endorse any vendor, product or service mentioned in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other rating. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, express or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.



