With the progress of the digital environment, new and more advanced electronic threats appear, which requires the strongest and most powerful cybersecurity measures. In recognition of this need, the National Cyber Security Authority (NCA) in the Kingdom of Saudi Arabia presented the basic cybersecurity controls (ECC) 2024 (ECC – 2: 2024), which is an improved version of the NCA ECC – 1: 2018 framework.
The ECC – 2: 2024 working is an important step forward in the cybersecurity strategy in the Kingdom of Saudi Arabia, which includes the latest security trends, addressing emerging threats, and ensuring compatibility with international cybersecurity standards. This updated framework provides a more powerful, comprehensive and developed approach to securing both traditional IT and modern technologies, including cloud infrastructure systems and industrial control systems. In this blog, we will discuss what the ECC -2: 2024 framework requires, and why it is necessary, and how QULYS can achieve the requirements of the ECC -2: 2024 framework.
Understand the NCA ECC 2024 framework
NCA ECC 2024 is a comprehensive set of cybersecurity controls aimed at protecting organizations from advanced electronic threats. This framework has been developed by the National Cyber Security Authority in the Kingdom of Saudi Arabia (NCA), and determines the minimum security requirements for entities in both the public and private sectors, ensuring the status of unified cyber security and flexibility.
Based on its predecessor, ECC – 1: 2018, ECC -2: 2024 includes improvements based on global cybersecurity standards, national regulations and lessons learned from previous cyber accidents. This development reflects the commitment of the Kingdom of Saudi Arabia to address the risks of cybersecurity in a proactive in a growing digital world.
The basic goals of ECC 2024
Enhancing cyberspace through critical sectors – strengthening defenses for government agencies, institutions and basic service providers. Unifying security controls – establishing a unified cybersecurity working framework to ensure consistent implementation through industries. Reducing the emerging threats – tackling the risk associated with cloud security, ransom programs, and chain chain citizen. Improving management and risk management – enhancing security supervision, compliance, and pre -emptive mitigation strategies.
The main areas of NCA ECC 2024 framework
The NCA ECC 2024 working framework has been organized around many critical cyber security areas, ensuring a strong and flexible security situation. These areas deal with the basic aspects of the Cyber Security Department, Governance and operational security. The main areas of the frame include:
1. Cyber security governance: developing policies, roles and responsibilities to ensure compliance with security standards. It enhances the culture of security perceptions through the specified governance structures. Effective governance assists organizations to manage risk and impose cybersecurity strategies. This guarantees a pre -emptive approach to controlling cybersecurity and organizational commitment.
2. Defending cybersecurity: focuses on securing assets, IAM, network security, encryption, and weakness. It includes 15 sub -range and 60 controls to protect critical systems. By carrying out layer security measures, organizations can reduce attack surfaces. This field enhances defenses against electronic threats through pre -emptive security measures.
3. Cybarian security flexibility: ensures the continuity of work by integrating cybersecurity in operations. It features four main controls that help reduce electronic disorders and accidents. Organizations can quickly recover from security violations and maintain basic services. This field focuses on reducing stopping time and ensuring operational stability.
4. Third security and cloud safety: It addresses the risks associated with sellers and cloud -based services to ensure data protection. It includes two sub -clubs and eight security controls for the security chain security. Organizations can reduce the risk of third party through strict security assessments. This guarantees safe partnerships and strong cloud security management.
NCA ECC 2024 provides cybersecurity organized approach, ensuring compliance and flexibility against advanced threats.
Compliance Challenge: Overcoming the main road barriers
NCA ECC 2024 provides a strong basis for cybersecurity, but organizations often face great challenges in implementing their controls. One of the basic obstacles is to adapt to advanced regulatory requirements. Checking for accurate planning and resource allocation requires, as institutions must set control elements, modernization policies, and align safety formations with new states.
Resources restrictions are another challenge, especially for small and medium enterprises (SMES) that may lack financial, technical and human resources needed to meet compliance obligations. Besides internal restrictions, organizations must also move in compliance with an external party and the supply chain. Verification that sellers adhere to the requirements of ECC 2024 adds the complexity, which requires institutions to assess the security practices of suppliers, verify compliance documents, and impose contractual obligations.
In addition, continuous monitoring and risk management remains decisive concerns. Compliance is not an effort for one time, but rather an ongoing process that requires a actual vision in the organization's cybersecurity. Determination of emerging threats and diluted weaknesses requires a conversion to traditional compliance methods, which often depend on periodic audits and manual assessments. In the scene of the dynamic threat today, organizations must adopt proactive solutions to constantly monitor assets, discover security bad operations, and evaluate risks in response to advanced threats.
Ensure NCA ECC 2024 compliance with the Qalys policy review
QUALYS audit enables organizations to achieve and maintain compliance with the NCA ECC 2024 framework. By automating compliance assessments and harmonizing security controls with ECC 2024 delegations, QUALYS audit of institutions helps to enhance its status in cybersecurity and address organizational requirements efficiently.
With the QULYS policy audit, institutions can assess their compliance status for ECC 2024 requirements, create detailed reports, and gain implementable visions in both technical and procedural security controls. This vision enables organizations to identify compliance gaps, implement corrective measures, and ensure compatibility with national cybersecurity directions.
The QUALYS policy audits provide a comprehensive library that includes 900 policies, 100 regulations, and more than 22,000 technical controls that extend to more than 400 technologies, including operating systems, databases, web applications, network appliances, protection walls and browsers. However, compliance ECC 2024 extends beyond technical controls – the requirements of the number include procedural measures and governance practices that require manual verification.
To address these procedural aspects, organizations can benefit from the Quals (SAQ) security evaluation questionnaire. SAQ offers a library of security questionnaires designed to assess non -technical controls, such as governance policies, third -party risk management, and data protection practices. By combining QUALYS audit of technical controls with SAQ procedural assessments, institutions can implement a comprehensive and end compliance strategy for ECC 2024.
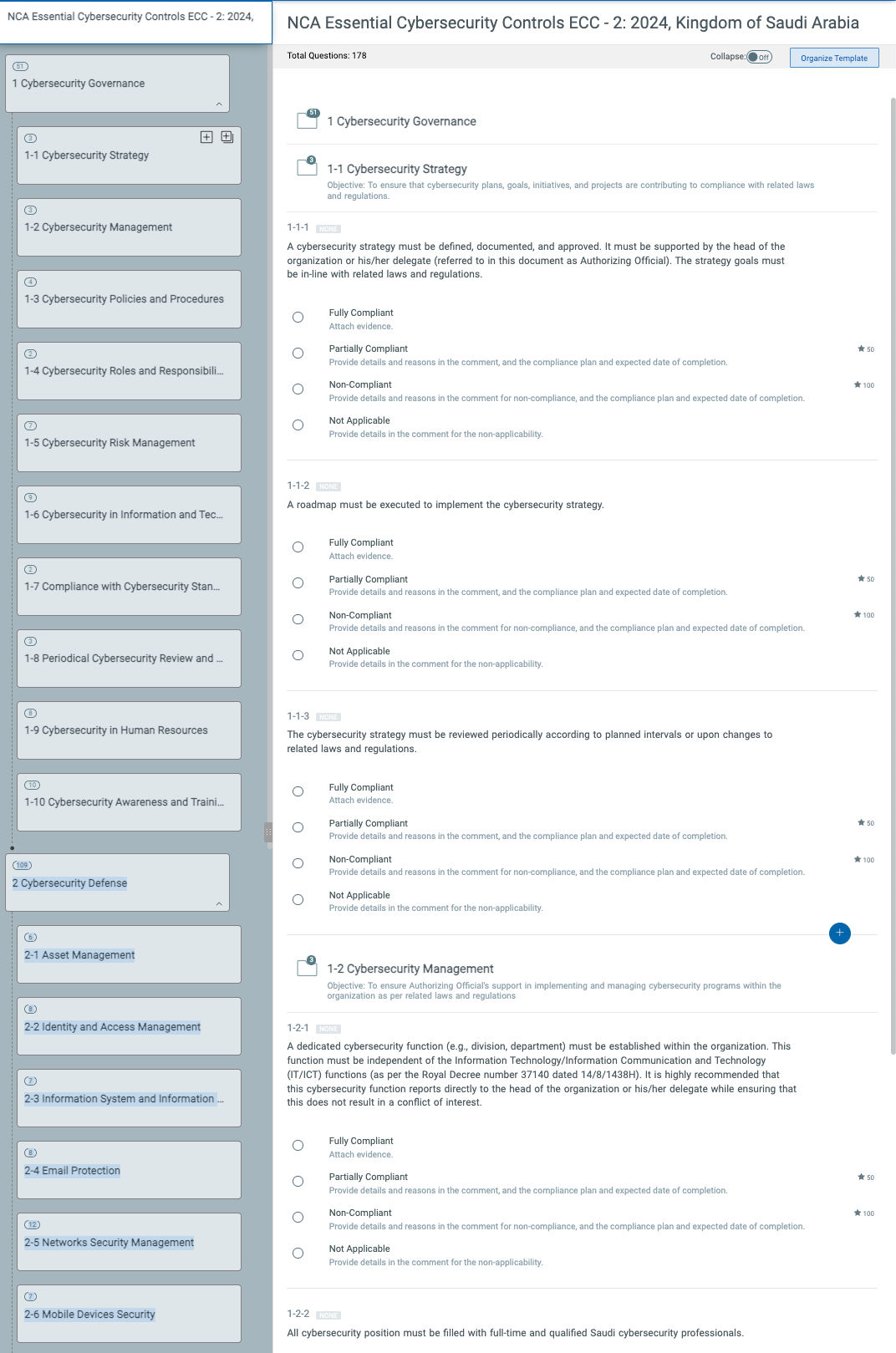
The Quals Enterprise TRURISKTM platform works as a unified solution, enabling institutions to automate compliance, simplify reports, and integrate cybersecurity risk management – all within one platform. This simplifies compliance efforts, reduces handicrafts, and ensures that organizations remain compatible with NCA ECC 2024 and other regulatory frameworks.
By adopting a script and SAQ for Qalys policy, institutions can efficiently navigate in the requirements of ECC 2024, enhance their security situation, and create a pre -emptive and continuous compliance approach in the sophisticated threat scene today.
To try how QUALYS Institutions Auditing can help comply with the NCA ECC 2024 frame, start today's experience.