Twenty-eight per cent of organizations witnessed a violation of cloud data or Saas last year-which led to the affected of more than 1 in 4 institutions. More worrying, 36 % of the affected people faced multiple violations within one year.
This is just one of many cloud security pain points that more than 100 practitioners shared in a recent study conducted by dark reading and Qalys. The image that appeared clear: The quick pace for adopting the original cloud-from artificial intelligence services to barefoot applications-excels the ability of many institutions to manage the safety risks.
Download the full dark reading report today to find out everything revealed by the research.
When the QUALYS (TU) Research Unit linked these visions practiced with our remote measurement, the results highlighted a pattern of repeated challenges: wrong discrimination operations that lead to the risk of filtration, weak assets exposed to public internet, and continuous Ransomwari threats, and engaging in compliance.
Let's dive into three basic visions of the search:
Insight 1: Self -cloud wounds
Despite the high development in the attackers' tactics, the number one danger is still amazing – 30 % human error. The wrongful cloud services continue to open doors for data violations, and the high infrastructure (IC) and the formations created from artificial intelligence are the amplification of these risks.
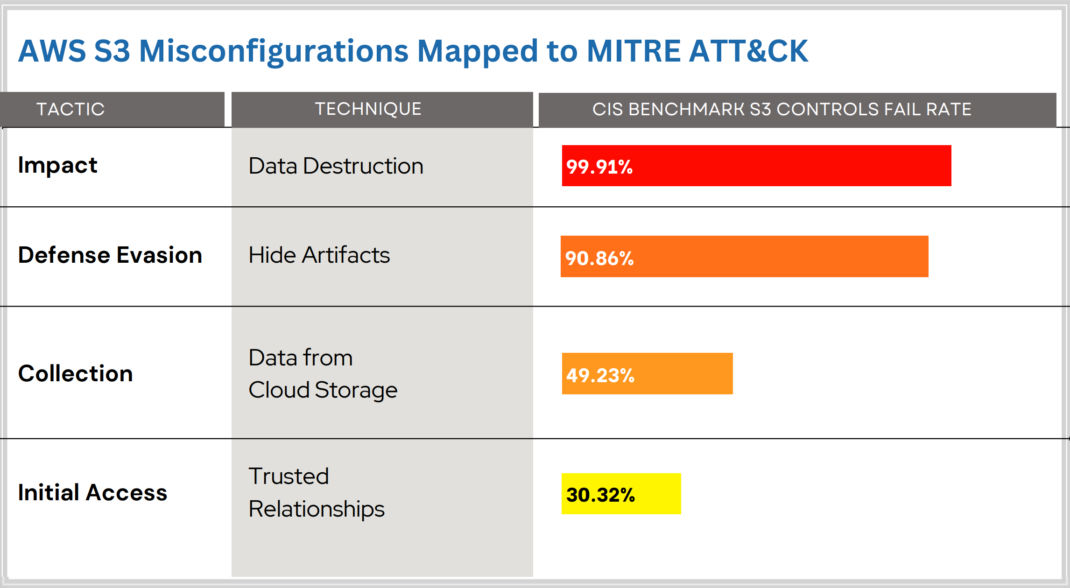
One blatant example: The wrong AWS S3 bucket performed 4,600 tests on the passport. These types of errors-whether manual or automatic-are exactly the reason why the ongoing wrong scanning, with the support of the implementation of a politician (for example, the standards of the Association of Independent Countries), must. In fact, as shown in the above data, 99 % of the apparent devices are not compatible with the deletion of MFA on the critical AWS S3 buckets in the cloud!
Moreover, these security lapses are often exploited through social engineering. Deceptive emails or malware on the human element, which leads to accreditation data at risk or unauthorized access. The bottom line: Reducing the surface of the cloud attack begins to manage poor formations proactively and educates users about the risk of hunting.

Insight 2: Skill gaps in responding to accidents
Even with security tools in place, organizations are struggling to respond effectively for violations. It is not technology – it's talent. The original cloud environments bring new variables-criminals, work burdens of artificial intelligence, and multi-missile networks-which overwhelm traditional books to respond to accidents (IR).

While the attackers automate the initial access and the side movement through the applications of application programming and open dependence, the security teams need a deeper vision and more intelligent automation. For example, in a recent TRU analysis of cloud blackmail attack, the open applications of the open application programming interface was used to get rid of sensitive data – all without standard discovery.
As shown in the data at the beginning of this blog, more than 3.9 meters+ VMS led to possible side movements. Security teams should start thinking like the attackers. It is necessary to assign potential exploitation paths from poor composition to settlement and integrate playing books directly into risk visions. The report explores how safety processes can merge this mentality through automation and directed treatment.

Insight 3: The growing cloud puzzle of Webaps and containers
Barefoot work burials and modern web applications have become an institution – but they also attend complex risks with rapid disappearance. Containers provide more connections between operations, exposed exposure to the network, and the changes of a quick life cycle that make traditional controls outdated.

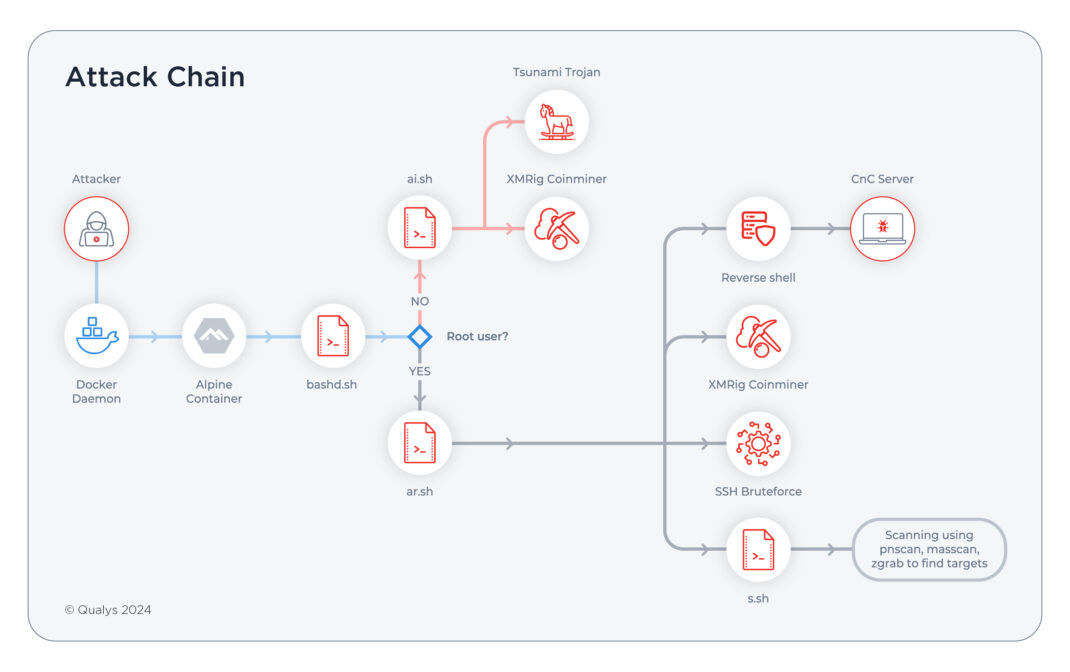
For example, QULYS TU recently unveiled from the open Docker Daemon ports in production environments, often stems from the DEV/Testing Test habits. These ports have been used in encryption mining attacks, confirming how wrong discrimination can quickly become weaknesses.
Add to that the wide use of third -party consequences, and the result is the surface of an attack that is constantly turning and is often invisible to traditional lights. The report is dinkened by practical strategies to close the container environments and impose policies before the work burden is going.
Read more
Conclusion: The danger of the cloud rises – but this is the opportunity to move forward
Modern cloud environments grow more complex, dynamic and – when mismanaged. From poor subordinate infrastructure as a symbol to the skills gaps in responding, security security and security spots, the risks are clear.
But this is the thing: these are only three of the main ideas that have been discovered in new dark reading research, which were developed in cooperation with Quales. When it is combined with the intelligence of the threat of threat research unit in Qales (TRU), the report presents a deeper look at how the security teams better understand – and work – expose them to risks.
Want the full image?
Download the full report to get the latest data, trends and fast food that will help you secure the cloud stack with confidence.
Interesting in learning more about Quales?
Join us at the Quals (QSC) security conference near you.
Talk to the Quals expert.
Shareholders
Abhinav Mishra, Director of Products Management, Container Security, Totalcloud CNAPP



