Securing the cloud has become more complex as organizations embrace hybrid and multi-cloud resources to meet their demanding business requirements. It’s also more important than ever: From 2022 to 2023, CrowdStrike identified a 75% increase in cloud breaches.
As organizations move their workloads and assets to the cloud, they need to take steps to protect sensitive data and ensure compliance across their Google Cloud environments. While Google Cloud is responsible for securing the infrastructure on which its services run, organizations that rely on that infrastructure are responsible for protecting their data within Google Cloud services—a process that includes critical steps such as implementing access controls, encrypting data, and monitoring for threats across the cloud.
Customer responsibility is what we cover in this blog post. Here, we highlight five best practices for securing Google Cloud resources, focusing on how CrowdStrike Falcon® Cloud Security can help you strengthen your cloud security posture along the way.
1. Implement strong identity and access management
Identity has become a primary target for adversaries—and a critical area of concern for organizations. The CrowdStrike 2024 Global Threat Report notes that 75% of attacks were malware-free in 2023, with stolen credentials a primary entry point. It’s clear that proper identity and access management (IAM) is the foundation of cloud security. Key IAM practices include creating and managing user roles, permissions, and access controls to ensure that only authorized individuals have access to sensitive resources.
Key strategies include:
Principle of Minimum Privilege (POLP): Grant users the minimum level of access necessary for their roles. Plan periodic assessments to reduce access levels when they are no longer necessary. Multi-factor authentication (MFA): MFA best practices add an additional layer of security. Implement session time limits, enforce strong password policies, and require regular password changes. Verify that MFA connections originate from a trusted source or IP range. Regular audits: Perform periodic reviews of IAM policies and permissions to detect and correct anomalies.
Implementing POLP, MFA, and regular audits makes it extremely difficult for attackers to steal and use credentials.
CrowdStrike Falcon Integration:
CrowdStrike Falcon integrates with Google Cloud IAM to provide real-time monitoring and alerts on suspicious activity. Its AI-powered insights help quickly identify and mitigate IAM-related risks.
2. Conduct continuous monitoring and detect threats.
Figure 1. Threat detections as seen on the Falcon platform
Identities aren’t the only way attackers can target resources in the cloud. They also look for configuration errors and vulnerabilities in the cloud, which they can use to gain initial access and move laterally across a victim’s cloud environment. Using threat intelligence, deep knowledge of attackers, and proactive threat detection are critical to identifying and mitigating potential security incidents before they escalate.
Continuous monitoring includes:
Real-time log analysis: Use Google Cloud logging and monitoring tools to analyze logs for unusual activity and capture and prioritize high-resolution alerts. While most logs are informational and lack direct security implications, high-risk attack logs require immediate action. Threat intelligence: Leverage threat intelligence to stay up to date on the latest threats targeting your cloud environments. Alert enhancement and automation: Enhance the quality of alerts with relevant data and context. This added information increases confidence in the importance of alerts, enabling more informed decisions during investigations. Set up automated alerts for anomalous activity that may indicate a breach.
Implementing continuous monitoring helps prioritize risks by identifying and mitigating the most critical threats, strengthening the overall security posture of your cloud environment.
CrowdStrike Falcon Integration:
The Falcon platform provides continuous monitoring with real-time threat detection and response. By connecting telemetry and detections through indicators of misconfigurations (IOMs), packet vulnerabilities, suspicious behavior, and threat intelligence, it helps organizations prevent, prioritize, and respond to threats.
Google Security Operations (SecOps) and CrowdStrike: Google Cloud’s SecOps security analytics engine integrates with Falcon, allowing security teams to more easily analyze endpoint and workload data to find and remediate threats. Teams can correlate bytes of data from Google SecOps with data sets from Falcon, enabling them to comprehensively investigate long-term, stealthy attacks across multiple surfaces and stop new and evolving threats.
3. Segment your cloud network
Cloud segmentation is a strategy that divides a cloud environment into smaller, isolated regions, each with its own security policies, controls, and access rights based on the sensitivity and importance of access to resources. This approach helps organizations reduce the attack surface and enhance security.
Key practices include:
Network segmentation: Divide your network into segments to limit lateral movement by attackers. Firewalls and security groups: Use Google Cloud firewall rules and security groups to control incoming and outgoing traffic. Security groups in cloud environments allow you to effectively segment your network. Security groups act as virtual firewalls, providing fine-grained control over traffic flow at the instance level. Private access: Restrict access to sensitive resources by configuring private Google Cloud IP addresses.
CrowdStrike Falcon Integration with Google:
BeyondCorp from Google Cloud shifts access controls from the network perimeter to individual users, enabling secure work from virtually anywhere without the need for a traditional VPN. It integrates with the Falcon Zero Trust Assessment, allowing joint customers to create and enforce granular application access policies using unique CrowdStrike risk signals. The integration enables seamless sharing of telemetry and data between the two security platforms, helping maintain the highest levels of security across a customer’s entire cloud or hybrid environment.
CrowdStrike Falcon® The Next Generation SIEM:
Falcon’s network security features complement Google Cloud’s native tools. They can be plugged directly into Falcon Next-Gen SIEM to provide detailed log analysis and anomaly detection to help quickly identify and stop threats, while providing remediation steps to simplify response for cloud security teams. Their integration with Google Cloud can help enforce security policies and monitor behaviors for potential threats in a customer’s environment.
4. Encrypt data at rest and in transit
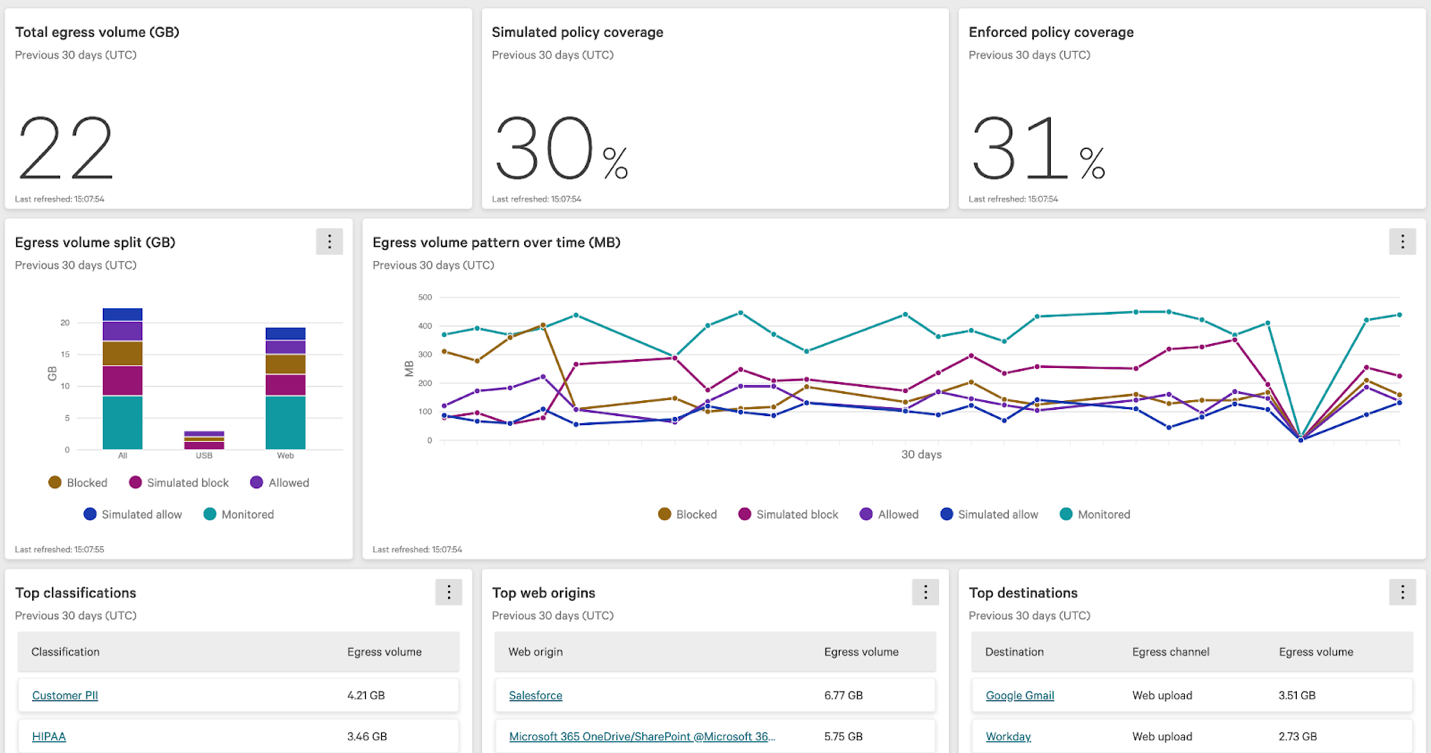
Figure 2. Monitoring data traffic across web applications to protect your sensitive data
Every reputable cloud provider offers basic encryption, a vital element of data security that ensures data is protected — even if it falls into the wrong hands. However, organizations must implement additional data security measures.
Best practices include:
Encryption at rest: Use Google Cloud encryption services to protect data at rest. Encryption in transit: Encrypt data in transit using SSL/TLS protocols. Key management: Implement strong key management practices, such as using the Google Cloud Key Management Service.
CrowdStrike Falcon Integration:
CrowdStrike Falcon enhances data security with advanced encryption capabilities. It ensures that data, whether at rest or in transit, remains encrypted and secure. Falcon’s encryption management system seamlessly integrates with Google Cloud’s native encryption services.
5. Implement strong compliance and governance

Figure 3. Simplifying cloud security with a central view of critical misconfigurations
Organizations handle massive amounts of sensitive data including customer information, proprietary business data, financial records, and intellectual property. To protect sensitive information and mitigate security risks, organizations must adhere to industry, national, and international regulations and frameworks, which help ensure robust security measures and prevent breaches. Failure to comply can result in severe penalties, loss of competitive advantage, and significant reputational damage. Organizations must prioritize cloud compliance to address security concerns, manage reputational risks, and maintain operational integrity.
This includes:
Compliance Frameworks: Adopt industry standard compliance frameworks such as GDPR, HIPAA, and PCI DSS. Regular Audits: Conduct regular security audits and assessments to ensure compliance. Policy Enforcement: Implement and enforce security policies across the organization.
CrowdStrike Falcon Integration:
Falcon Cloud Security covers four major security compliance frameworks, including MITRE ATT&CK®, CIS, NIS, and ISO, as well as industry-specific requirements, including GDPR and PCI DSS for financial services and payments, FedRAMP and FISMA for government, and HIPAA and HITECH for healthcare. With Falcon Cloud Security, you can identify risks and vulnerabilities, remediate misconfigurations and vulnerabilities, and enforce gold-standard policies to meet industry regulations while securing your business in the cloud.
Falcon Cloud Security: The Perfect Solution for Google Cloud Users
CrowdStrike Falcon Cloud Security is an exceptional solution for securing Google Cloud resources. Its powerful features, seamless integration with Google Cloud, and AI-powered insights provide unparalleled protection. By implementing these best practices, organizations can ensure that their Google Cloud environment remains secure and compliant.
Key Benefits of CrowdStrike Falcon:
Seamless Integration: Easily integrates with Google Cloud services. AI-powered Threat Detection: Uses AI to detect and respond to threats in real time. Comprehensive Protection: Provides end-to-end security, from identity and access management and network security to data encryption and compliance.
Securing your Google Cloud resources doesn’t have to be a daunting task. With CrowdStrike Falcon Cloud Security, you can protect your environment with confidence, knowing you have a powerful ally on your side. Implement these best practices today to take your cloud security to the next level.



