With Gartner recently announced that SOAR (security, automation and response coincidence) is disposed of in favor of artificial intelligence solutions, this article will explore in detail four cases of using the main safety automation.
1.
IOCS indicators, such as suspicious IP addresses, fields, and retail files, are vital in determining and responding to security accidents.
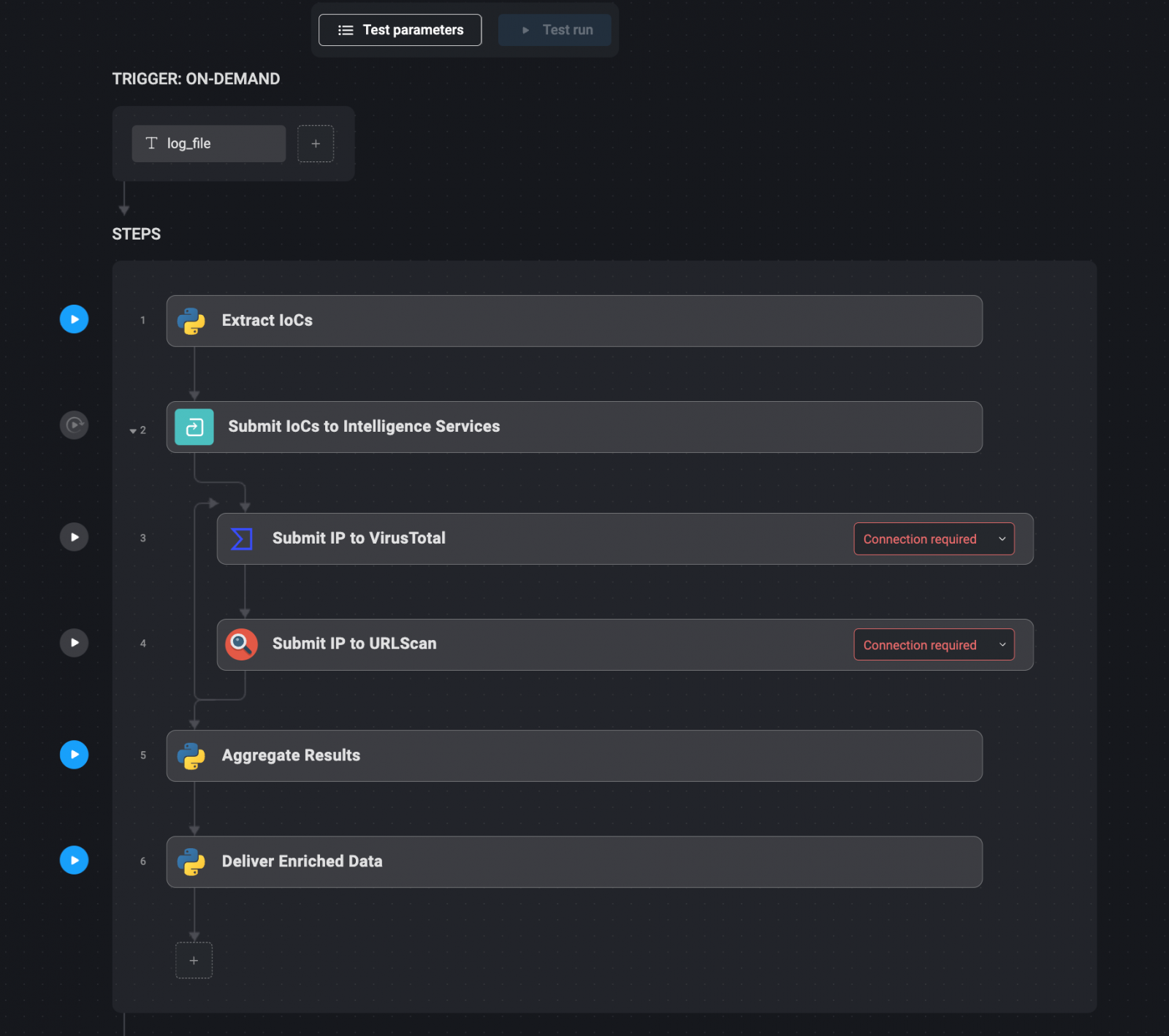
The collection of information can be manually about this IOCS from various sources of employment and slowing the response process.
IOCS automation can significantly enhance the efficiency of your safety operations.
Automation workflow:
IOCS extraction: automatically relevant IOCS extract from safety records or alerts using text analysis tools or other automated methods. IOCS to Intelligence Services: Once you are extracted, IOCS is automatically provided to various threat intelligence services, such as Virustotal, URLSCAN and Alienvaut, via their applications of their application programming. These services can provide an additional context, such as whether the IP address has been associated with known threats or whether the field has been marked with suspicious activity. Total results: The results of these intelligence services are assembled in one comprehensive report. This step guarantees that all relevant information is available in one place, making it easier for security analysts to assess the threat. Incredible data delivery: Fertile IOC data is then delivered through communication channels such as Slack, or added directly to the relevant accident ticket within the safety management system. This ensures that all the necessary information is immediately available to those who need it.
2. Monitor your external attack surface
The surface of the institution's external attack includes all the external assets that attackers can take advantage of.
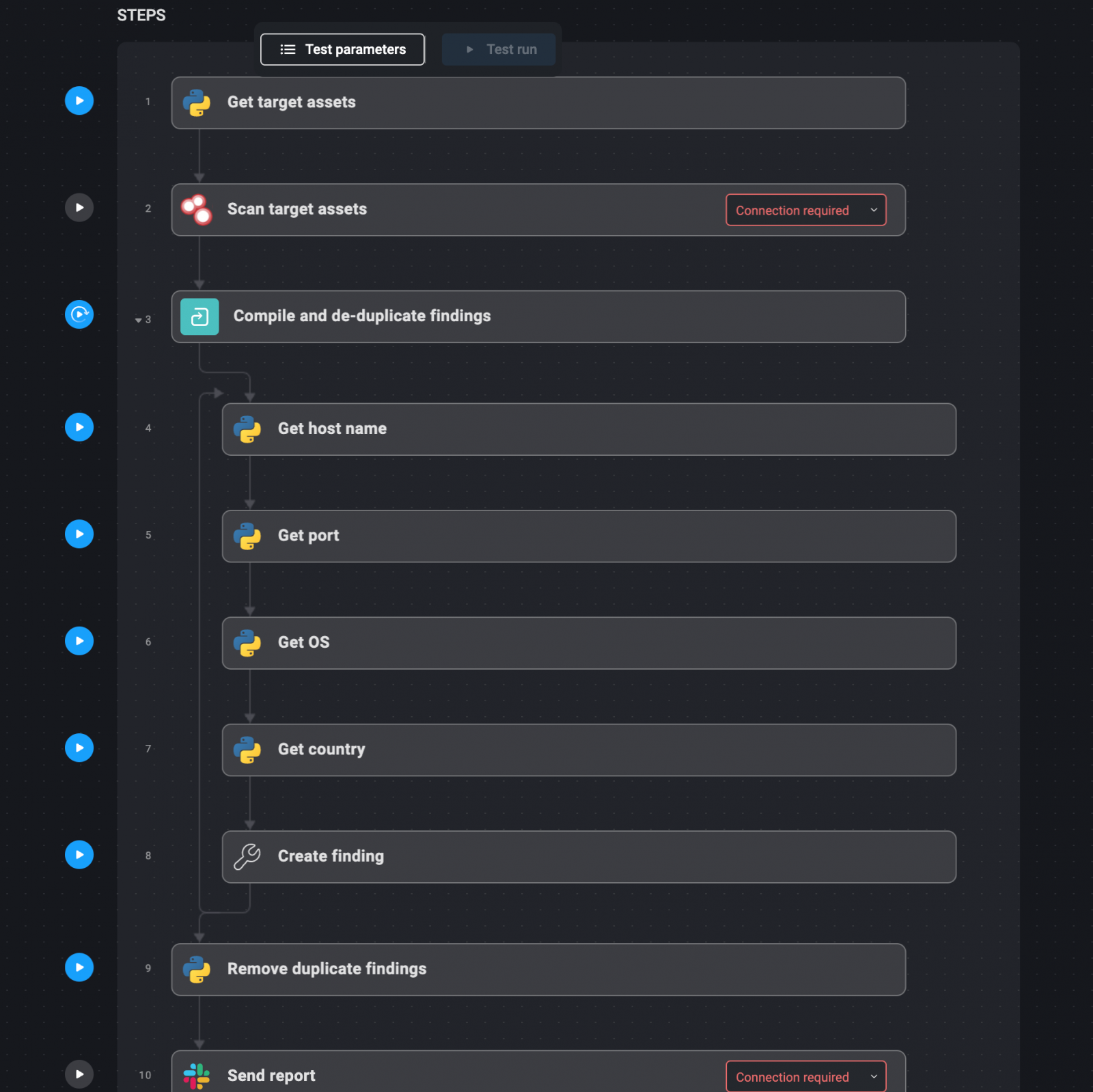
These assets include areas, IP addresses, sub -ranges, open services and more.
Regular monitoring of these assets is important to determine and reduce potential weaknesses before exploiting them.
Automation workflow:
Determining the target assets: Start by identifying areas and IP addresses that make up the surface of the external attack. These must be documented in a file that the automation system can refer to. Automated Poll: Use tools like Shodan to wipe these assets on a weekly or monthly basis. Shodan can help identify open ports, open services and other weaknesses. Translation of results and re -blogging: The results of these scannings are automatically assembled in a report. Any repeated results are removed to ensure that the report is brief and executed. Weekly reports: The final report is delivered via e -mail, recession or another favorite communication channel. This report sheds light on new or variable assets, potential weaknesses, and any extra applications that may pose a danger.
3. Survey to weaken web applications
Web applications are frequent targets for attackers, making regular weaknesses useful for maintaining safety.
Tools like Owasp Zap and Burp Suite automate the process of identifying common weaknesses, including old programs and poor formations.
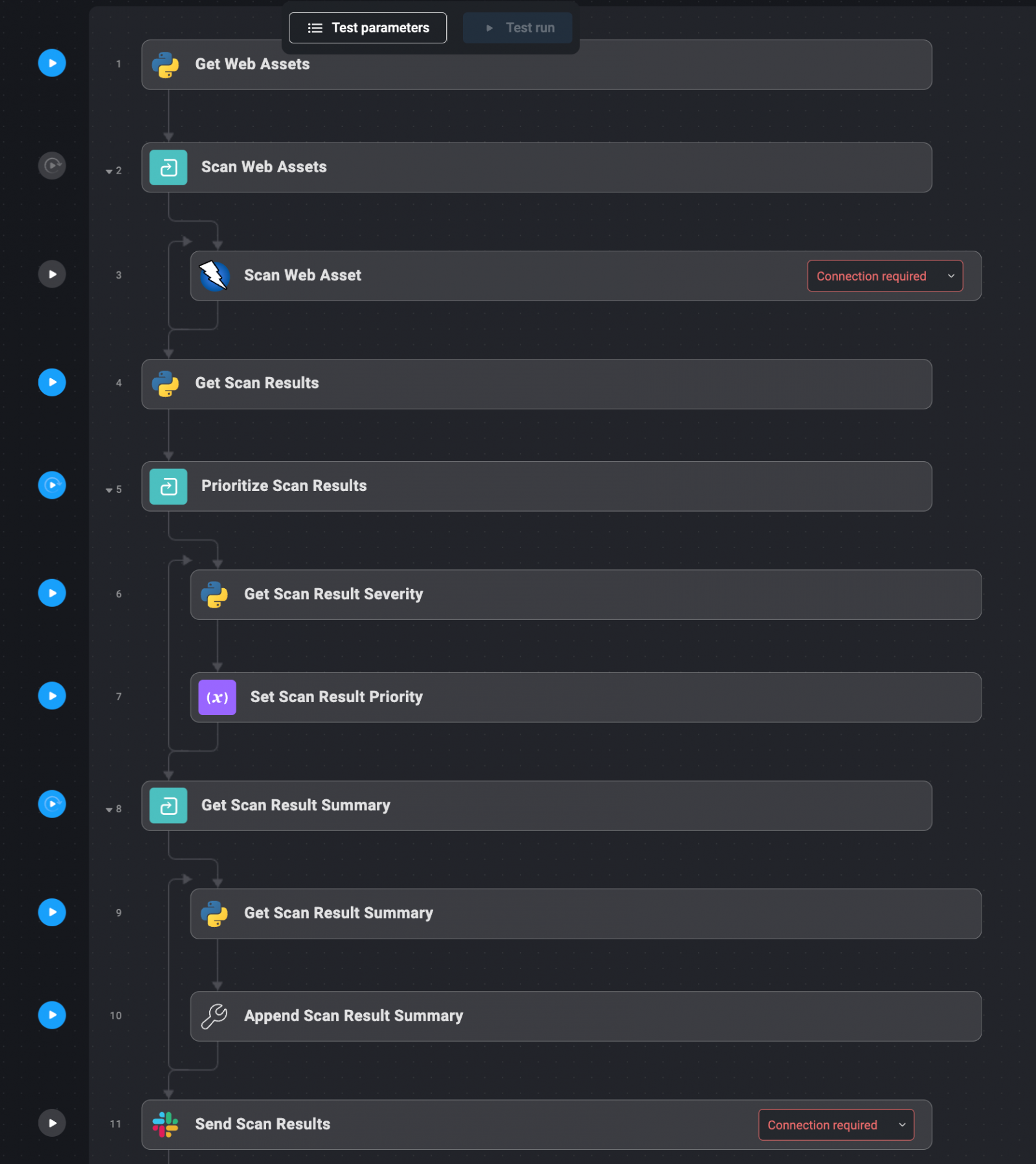
These scannings also discover the weaknesses to verify the health of the inputs, which helps to secure web applications.
Automation workflow:
Select web assets: Start by inserting all areas and IP addresses that host your organization's web applications. These assets should be documented in a file for ease of reference by automation system. Automatic scanning: automatically defined web assets are sent to surveying tools such as Owasp Zap and Burp Suite. These tools perform comprehensive surveying operations to determine weaknesses, including those that are commonly exploited by the attackers. Gathering results and setting their priorities: The results are collected from surveying operations automatically and their priorities are determined based on the severity of the discovered weaknesses. Critical/sharp weaknesses are highlighted. Reconciliation of the results: Priority results are delivered to the relevant teams via Slack or as a fertilized ticket within the accident management system. This ensures that the right persons are notified of weaknesses and can take appropriate measures.
4. Monitor email addresses for stolen credit data
Monitoring the risk accreditation data is an important aspect of the organization's cybersecurity strategy.
Are you PWNed (HIBP) is a wide -use service that collects data from various violations to help individuals and institutions determine whether their accreditation data has been hacked.
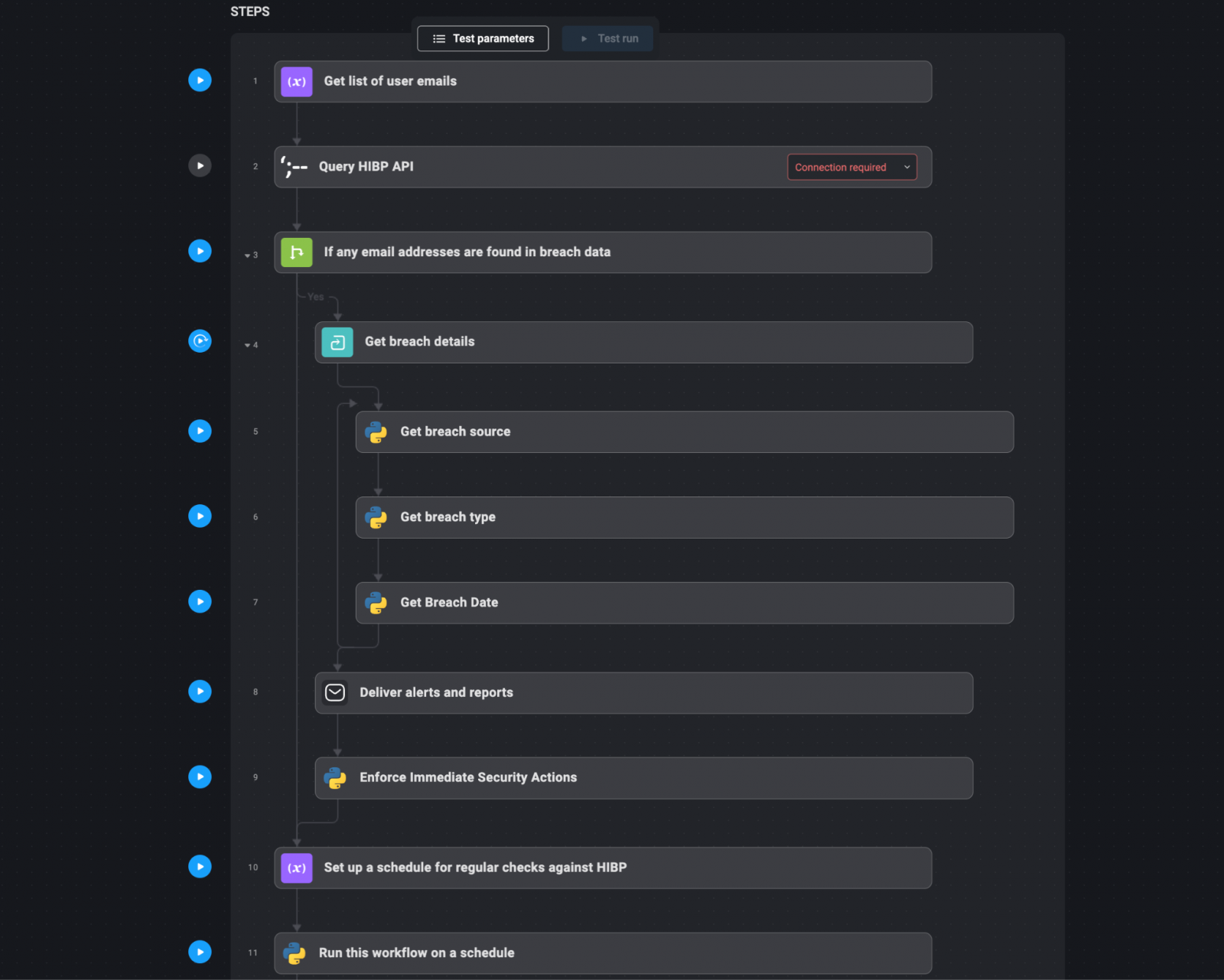
The automation of the HIBP check for open credentials can help institutions identify and respond to potential security incidents.
Automation workflow:
Collecting emails and fields for the user: Create a list of email addresses or areas that need to be monitored. This list should include all relevant user accounts within the institution, especially those with distinctive access. HIBP API: Automatically query in the HIBP applications interface with an email address or translated fields. This step includes sending requests to HIBP to verify whether any of the email addresses have appeared in known data violations. Assembly and Results Analysis: Collecting responses from HIBP. If any email addresses or areas of penetration data are found, details of these violations (such as a breach source, the type of open data, and the date of breach) are collected and analyzed. Delivery of alerts and reports: If exposed accreditation data is discovered, create an alert automatically. This an alert can be sent via email, stagnation or built -in in the organization's accident response system as a high priority ticket. Include detailed information about the breach, such as affected email addresses, exposure nature, and recommended procedures (for example, the password reset). Importing immediate security measures: based on the severity of the breach, the system can automatically impose safety measures. For example, it may lead to the reputation of the password for affected accounts, notifying the concerned users, and increasing monitoring of the hacked accounts. Regular scheduled checks: Prepare a schedule for regular checks against HIBP, such as weekly or monthly queries. This ensures that the organization remains aware of any new violations that may include its approval data and can respond immediately.
Related questions
Below, we will answer some of the questions circulating about the automatic workflow above and how they can help in a practical way.
Doesn't the third -party services provide a workflow to automate anyway?
Several services provide application programming facades that allow the automation of parts of the workflow, such as bringing data. However, the creation of automatic workflow to the tip of coding and configurations requires. It provides the recurrence of the entire workflow with flexible but less powerful textual programs, as changes can break it. It provides the use of the applications available available with a central automation platform a stable and developed solution. Can we not repeat this entire matter with Bash texts?
Yes, it is possible to write the texts of Bash/PowerShell to automate the safety tasks mentioned in the article. Text programs offer flexibility that lacks manual processes. However, the textual programs require continuous maintenance, and any changes that can break the workflow. They may also lack advanced features such as central administration, schedule, alert and reporting, which are presented by customized automation platforms such as Blink Ops. The appropriate platform is more reliable and effective for long -term automation requirements. How to help automation to enrich IOC?
IOC enrichment automation speeds up the response process by collecting the intelligence of the threat to indicators such as IPS, fields, and retail files from multiple sources simultaneously through application programming facades. This provides the security teams a single comprehensive report with the context necessary to quickly evaluate threats, instead of spending time manually searching in various sources. It improves circumstantial efficiency and awareness, allowing quickly enlightened decisions.
Improving your position on cyberspace with OPS flash
BLINK is a multiplication of the strength of the return on investment for security teams and business leaders who want to secure a wide range of cases of use quickly and easily, including SOC response and accident response, weakness, cloud security, identity management and access, governance, risk, and compliance.
With thousands of automation in the Blink Library and the ability to customize the workflow to suit your specific condition, Blink OPS can significantly improve your safety processes.
Start with Blink Ops.
Written by Blink Ops.



